Security firm K7 Security Labs reported that hackers ironically used the official Windows bug reporting tool to spread malware. Because an original version of the program is used for the scam, it goes unnoticed by most antivirus and antivirus software.
The trick starts with the victim receiving an ISO file (disk image) via email. When you double-click the file, it mounts itself as a new drive containing the legitimate Windows error reporting program called WeFault.exe. Clicking on this file starts the infection, but it is not the file that is infected with the malware.
In the case of this trick, the executable is truly genuine and harmless. The scam is in the errorrep.dll file which is also in the hackers ISO. This is another official Windows file normally used by your bug reporting tool – but in this case, errorrep.dll is contaminated with malicious code.
Running WerFault.exe from the ISO will load the “closer” errorrep.dll file, which is still in the package. This trick even has a name: “DLL sideloading”. On the face of it, the program will run as it should, but a Trojan horse known as Pupy RAT will also be installed.
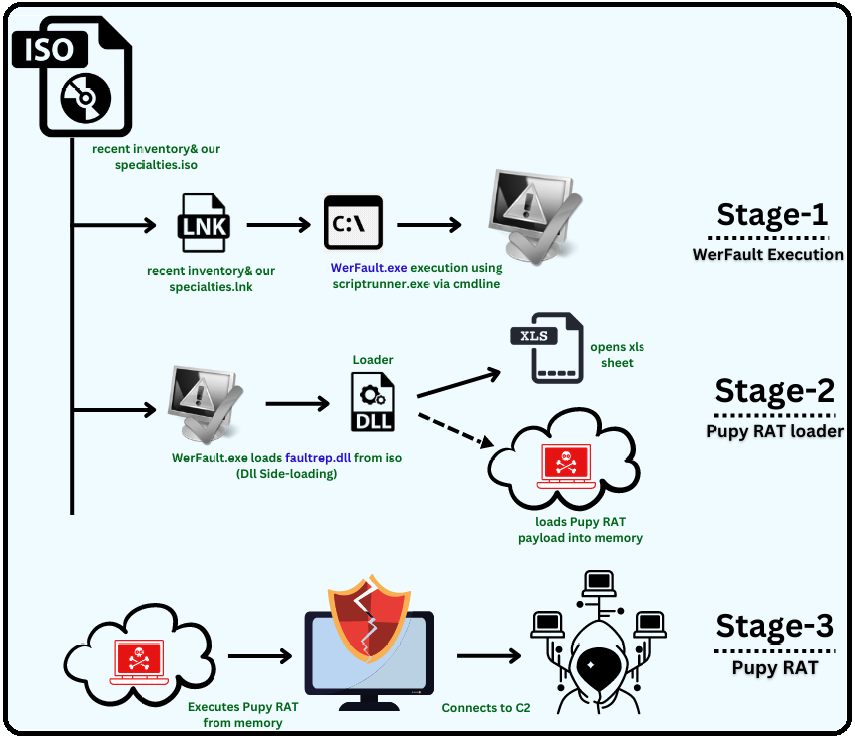
Pupy RAT can execute remote commands on the infected system, steal data, install other malware and also infect more computers in the network.
This is a dangerous scam that most likely won’t be detected by your antivirus. It is therefore recommended that you always take extra care when downloading executable files from the internet and also carefully check the sender of your emails. Scammers specialize in impersonating official accounts to send emails, but it often takes a watchful eye to know when that’s the case.
Source: Tec Mundo