A security breach at META’s direct supplier exposed the data of all employees of the North American technology group. The information includes full name, position, email, password and work address.
Failure affects not only META in Brazil, but the entire world. The company is responsible for services such as Facebook, Instagram and WhatsApp.
According to security researcher Marlon Fabiano (Astrounder), the flaw also affected the data of top META executives, including CEO Mark Zuckerberg. Specifically, 83 thousand pieces of data were found in his research.
The vulnerability found at the supplier revealed not only personal information, but also confidential documents containing training, market opportunities, company infrastructure, tools used and other details.
META was alerted to this vulnerability and the issue has been fixed. The supplier was not disclosed upon the company’s request.
In conversation with TecMundoAstrounder commented that the vulnerability is known as a “supply chain attack.” Access to the application was provided through a technique called “password spray”.
Surprisingly, the META vendor did not use a second authentication factor on the accounts. In addition, it was possible to change the user ID logging in to the URL and obtain information from other META employees through the settings in the application.
Astrounder said it even downloaded data from 83,000 employees to take to META as proof of impact. After the warning, the company asked the researcher to terminate his employment and said the effect had already been proven.
The terms and processes used will be explained below. HE TecMundo We contacted META for a position on the case; This position will be added when we receive it.
changing children
Supply chain attacks involve targeting suppliers of large companies. This means that even if a large company has cybersecurity as a priority, a third-party vendor may not have that priority, opening a loophole for sensitive information and personal data.
Regarding the use of the technique, Astrounder commented: “Companies remember to spend a lot of resources on technology and lately on raising awareness among their employees, but one thing is still overlooked: the risk that outsourcing brings to the organization. However, it can cause various effects called supply chain attack.” “We have a vulnerability that could be possible. However, we are faced with two main types of attacks: software and hardware, in addition to service providers. The aim of the attack is to choose the path of least resistance to the target of the attack.”
- The attack flow occurs as shown in the image below:
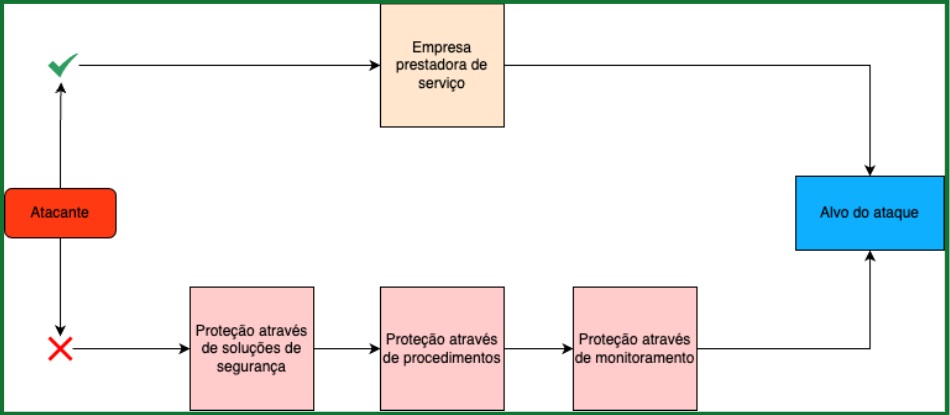
The researcher explains that using this type of attack, it is possible to detect one of Facebook’s third parties and infect an application under the company’s Bug Bounty program.
Bug Bounty is a form of support that companies have developed for security researchers to safely report flaws in their services.
“By enumerating the supplier’s subdomains, it was possible to identify an application that displays a login screen (email) and password for Meta employees. There are various tools and applications that can assist with the task of enumerating and discovering login information. Linkedin is a very useful application in these situations; because emails can be created with first and last name or patronymic patterns as well as the name followed by the organization’s domain. For example: “name” + “.” + “aboutname”@domainofORG.com. “Only with publicly available data is it possible to obtain a list of valid emails using publicly available sources,” Astrounder added.
After this process, the researcher noted that the most important point was still missing: the password.
“For passwords, it is possible to use patterns like “Empresa@ano” or a variation of it. There are very useful tools for this, such as https://github.com/sunw4r/weakpass. It always matches the password pattern used by third parties. Now the username and possible “A password attack can proceed through a brute force or password spray attack.”
The use of a supplier without cyber security weakened all of META’s efforts in this regard
What is a password spray attack? Also known as a password spraying attack or mining, this method is an automated technique used to obtain valid access credentials. It commonly involves trying the same password on different user accounts and then trying another password.
As mentioned previously, it is important to note that META employee credentials at the vendor do not have a second factor of authentication (MFA/2FA) enabled. “This made the attack much easier,” the researcher added.
Program prioritization had not acknowledged the error due to lack of impact. “So by changing the ID in the URL directly in the app, I dumped the employees’ data until I identified the email of the representative who scanned the report. While PoC (documented proof) was sent that it was possible to get the data from whomever I wanted (including the screening agent), a request was made to stop the research because the effect had already been proven”.
This case reveals various security weaknesses that concern small companies, huge conglomerates, and even our personal security.
The use of a supplier without cyber security weakened all of META’s efforts in this regard. By developing a simple employee ID numbering and not enabling the second authentication factor, the supplier will be wading through turbulent waters in handling this case with META.
Finally, I hope this report reaches you as a reminder that you need to enable the second authentication factor on all accounts. Use a third-party app for this: Google Authenticator, Microsoft Authenticator, Authy to name a few. Avoid 2FA via SMS.
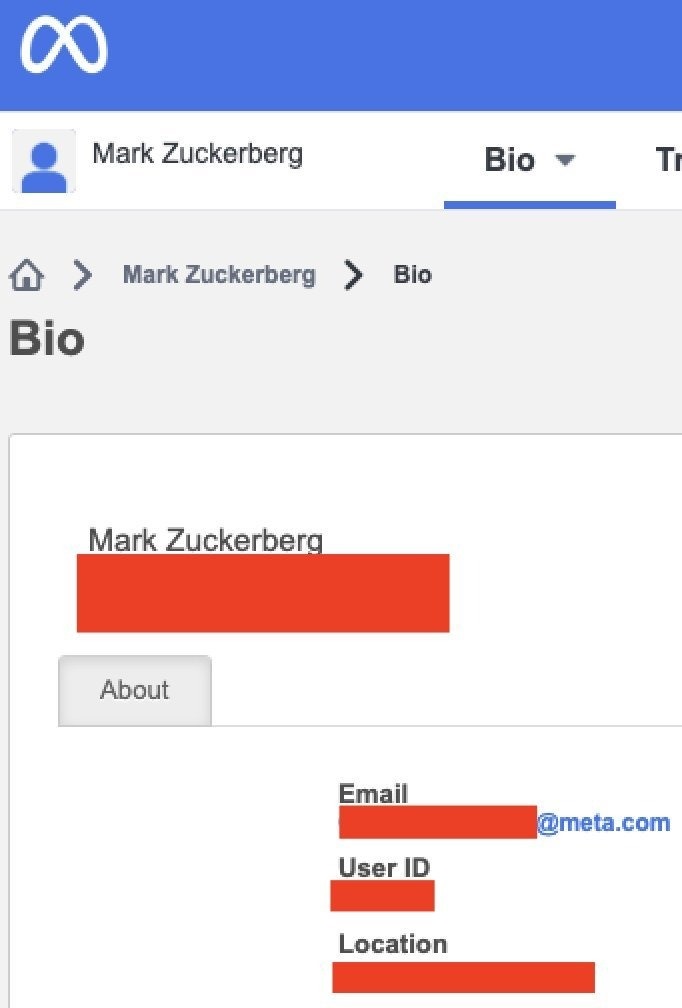
Report to TecMundo
HE TecMundo It supports the ethical work of hackers. Our communication channels are:
Source: Tec Mundo
I am a passionate and hardworking journalist with an eye for detail. I specialize in the field of news reporting, and have been writing for Gadget Onus, a renowned online news site, since 2019. As the author of their Hot News section, I’m proud to be at the forefront of today’s headlines and current affairs.