Bleeping Computers reports that two serious vulnerabilities have been discovered in Bluetooth to intercept connections.
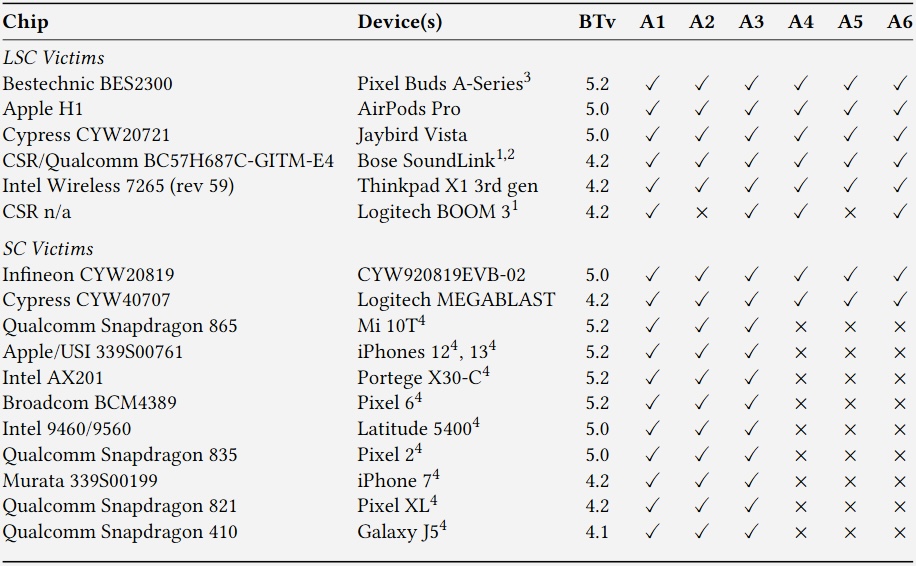
These flaws are architectural, meaning they affect Bluetooth at a fundamental level. The issue is tracked under CVE-2023-24023 and is dependent on the Bluetooth Core Specification 4.2 through 5.4.
The new series of exploits is called BLUFFS. They are aimed at hacking and reducing the confidentiality of Bluetooth connections, stealing personal data and more.
BLFFS uses two previously unknown methods in the Bluetooth standard related to the topic, such as established session keys to decrypt the data in the exchange. four extensions (two new ones) are used in the key session inference process to provide short, weak, and low-cost key session (SKC) inference. The attacker then embeds a small key that allows him to decrypt messages and manipulate all future communications.
This allows two types of processing:
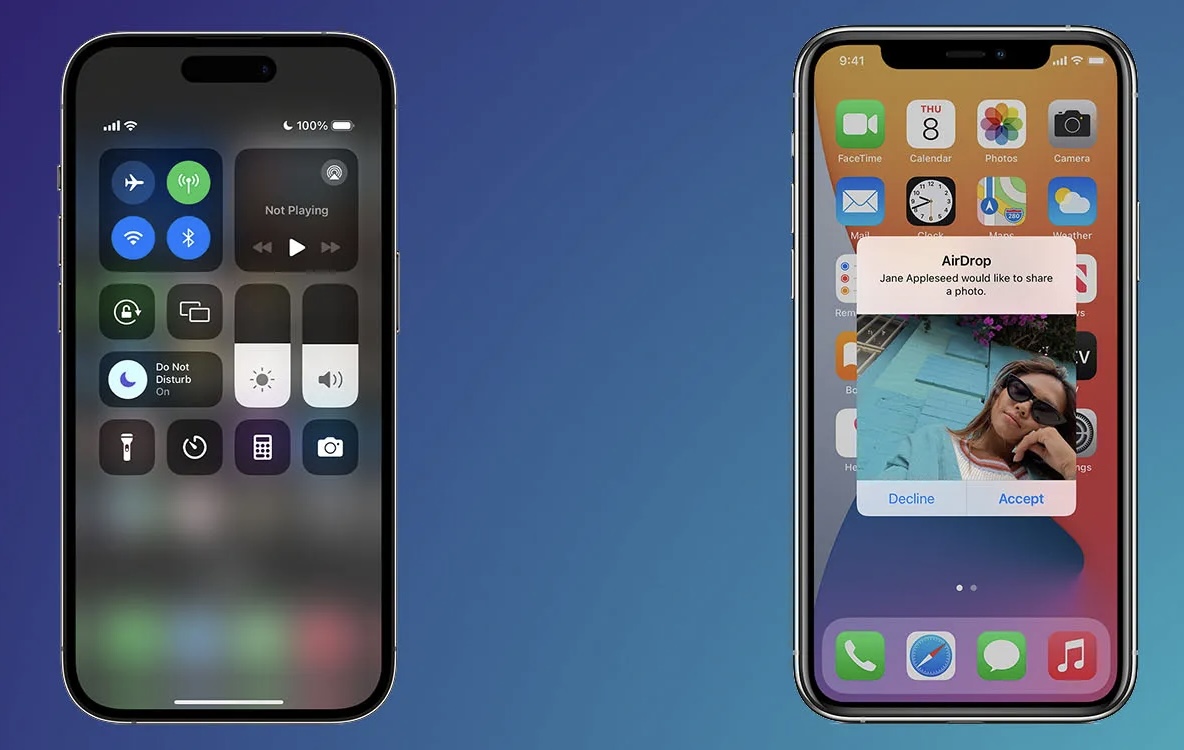
• Imitation. When you think you’re sending data to a known device (for example, via AirDrop), you’re actually connected to the attacker’s device.
• Man in the Middle (MitM) attack. When you send data to the intended device, it is intercepted by the attacker, so it is copied.
All devices using Bluetooth 4.2–5.4 are vulnerable to vulnerabilities. There is no solution to the problems, just update the standard. To minimize risks, it is recommended to turn off Bluetooth in public places unless necessary. [9to5]
Source: Iphones RU
I am a professional journalist and content creator with extensive experience writing for news websites. I currently work as an author at Gadget Onus, where I specialize in covering hot news topics. My written pieces have been published on some of the biggest media outlets around the world, including The Guardian and BBC News.