Windows Task Scheduler is used by malware to hide itself. This hacking tool called Tarrask uses a previously unknown bug to delete the Security Descriptor registry. As a result, the malicious process is not detected by the scheduler. Thus, access to hacked devices is preserved even after rebooting.
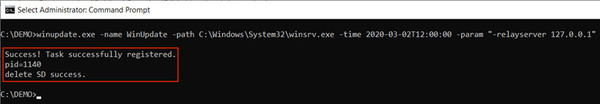
Microsoft writes this in a blog post to raise awareness about the attacks. These come from Hafnium, a Chinese government-sponsored group that is part of Microsoft Exchange Meltdonw. The enormous amount of data released would be used by China for AI development. Tarrask software is used to keep malware-infected systems vulnerable undetected. The whole process can also be removed for this, but after a reboot, access is lost.
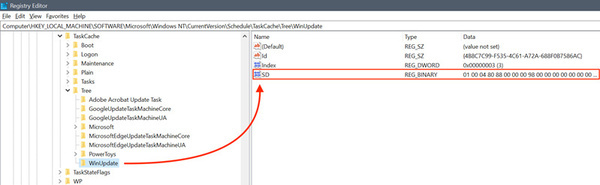
Hidden tasks can only be found manually by searching the Windows Registry for tasks that do not have a security descriptor value in the Task Key. The Security.evtx and Microsoft-Windows-TaskScheduler/Operational.evtx logs may also indicate that these tasks are hidden. The manufacturer recommends close monitoring of links to sensitive data. Also, no definitive solution is provided for the error.
Source: Bleeping Computer
Source: Hardware Info











