Today we take a journey through the gaming industry, to a time when there was no Denuvo, StarForce and other anti-piracy programs known today. And this does not mean that chaos and lawlessness reigned in the games market.
It’s just that copy protection methods have sometimes been so unusual and harsh that modern protection systems may seem too lenient to you. Make yourself comfortable, I will tell you about the most unusual and interesting ways to combat piracy.
Short description
Unique file table
Logo and hole on a floppy disk
Hardcore Survival Horror instead of JRPG
Breaking the fourth wall
Conclusion
◦ Back to contents ◬
1. Microsoft Adventure and its unique file table.
 This is what the cartridge for the first pirated game looks like.
This is what the cartridge for the first pirated game looks like.
The first officially documented case of copy protection was the method used to protect floppy disks containing the text game Microsoft Adventure. In those years, floppy disks did not have any copy protection.
Microsoft developed ready-made table files that were significantly different from the structure of a regular floppy disk. Initially, programs for copying floppy disks provided the following provisions: all floppy disks were formatted in a standard format, so it was enough to simply copy all the files from the file tables to the corresponding tracks and sectors.
However, for adventure, as I already mentioned, there was file system.
Only the Adventure launcher itself knows how it is read, and other programs cannot do this since they are designed for standard formation. Because of this, attempting to read any other program’s floppy disk would fail.
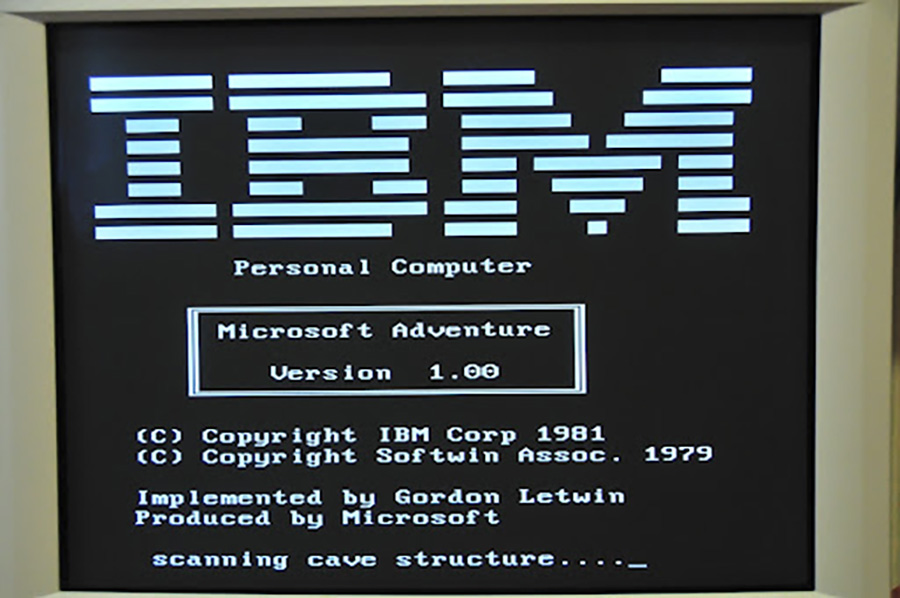
On a non-original cartridge, the game did not start further in this window.
Later, this protection method was bypassed by decrypting the file table. This method of protection quickly becomes obsolete unless you rotate the lid to create a backup latch in case the floppy disk is damaged or the game cannot be installed on the computer drive.
It was replaced by a more interesting method of protection.
◦ Back to contents ◬
2. Logo and hole on floppy disk as tax verification tool.
 Floppy disk with the game in a unique case.
Floppy disk with the game in a unique case.
Nintendo has proposed another interesting way to protect a disc from copying. They designed a special enclosure for their floppy disk that fits perfectly into the Famicom Disk System.
However, in any other floppy disk in this case it was impossible to insert.

The game requires the original floppy disk to be inserted.
But the most interesting thing is that the Famicom Disk System had a floppy disk authentication system installed. If the defendants inserted any floppy disk other than the original one, which had the inscription “NINTENDO” on it, the system generated an error.
Other companies used relatively similar protection methods. For example, some manufacturers tested the license by causing a read error during gameplay. To do this, the floppy disk was drilled in a certain place.
This method of protection was difficult to circumvent for objective reasons. After all, you didn’t know which files were located in the drilled area.
◦ Back to contents ◬
3. Turning a cute JRPG into hardcore survival horror
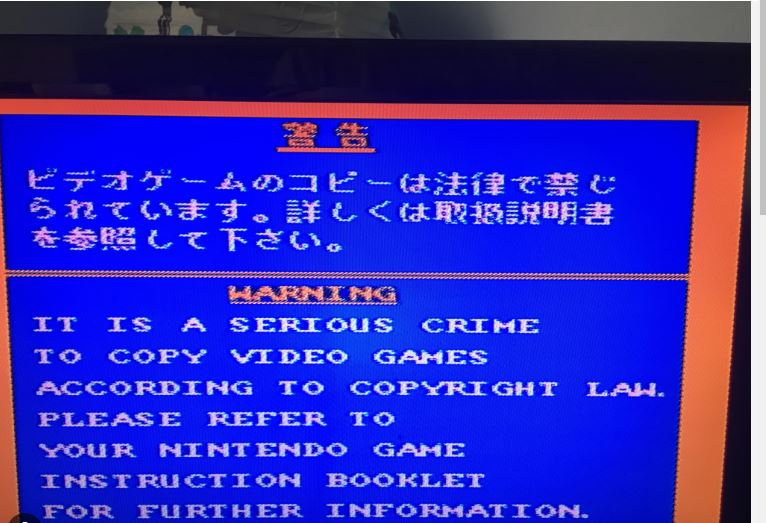 A warning that it was displayed if a non-original copy of the game was launched.
A warning that it was displayed if a non-original copy of the game was launched.
But let’s talk about something more interesting. In our area this game is not very weak, but in the West it is considered a cult game. I’m talking about Earthbound – bright role playwhich comes out on the Super Nintendo.
In the story, a group of guys fights aliens who are trying to take over their hometown. The game is filled with bright colors, humor and fun, with the exception of the rather creepy and surreal last location and final boss.
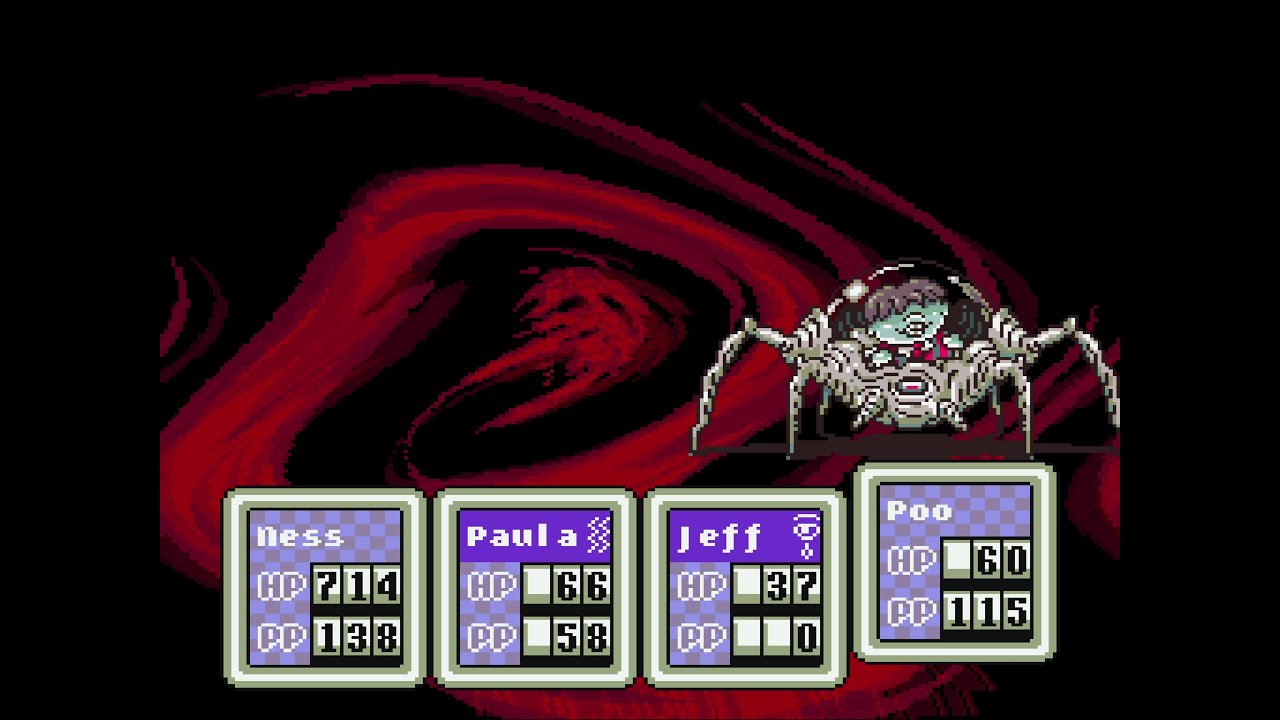 The last frame the player saw in Earthbound before the system reset the testing progress and rebooted the game.
The last frame the player saw in Earthbound before the system reset the testing progress and rebooted the game.
However, Nintendo made the game even more dangerous for pirates. If the game did not pass the test, it would still start, but the difficulty of the battles increased many times over. Each encounter was literally a mortal danger; any mistake would throw the player back to a checkpoint.
But even if the player masters the game to the final, then before the fight with the boss she hung out with scary music, restarted and deleted all saves. This is what it looked like:
Even watching this, it becomes creepy and creates an atmosphere of cursed games from scary stories.
I can’t even imagine the emotions of a person who mastered the game and faced such a setback at the end.
◦ Back to contents ◬
4. Breaking the fourth wall as a way to protect against pirates
 The kit included a booklet, information from which had to be used in the game itself.
The kit included a booklet, information from which had to be used in the game itself.
In this section, we’ll look at examples of how games interact with the player, going beyond the story and addressing it directly.
This can be called “breaking the fourth wall.” Sometimes this interaction occurs within the plot itself, sometimes in the form of a separate message.
 In this dialogue, you had to put a real letter from a cartridge box into the water to enter the game, which revealed paper information.
In this dialogue, you had to put a real letter from a cartridge box into the water to enter the game, which revealed paper information.
For example, in the game Star Tropics for NES, just like Dendy, about halfway through the message you need to dip the letter in water. If you don’t do this, there will be no plot.
But where can I get this letter? It turns out that it comes with the cartridge. You need to dip a piece of paper in water, and hidden text will appear on it with a hint on what to do next.
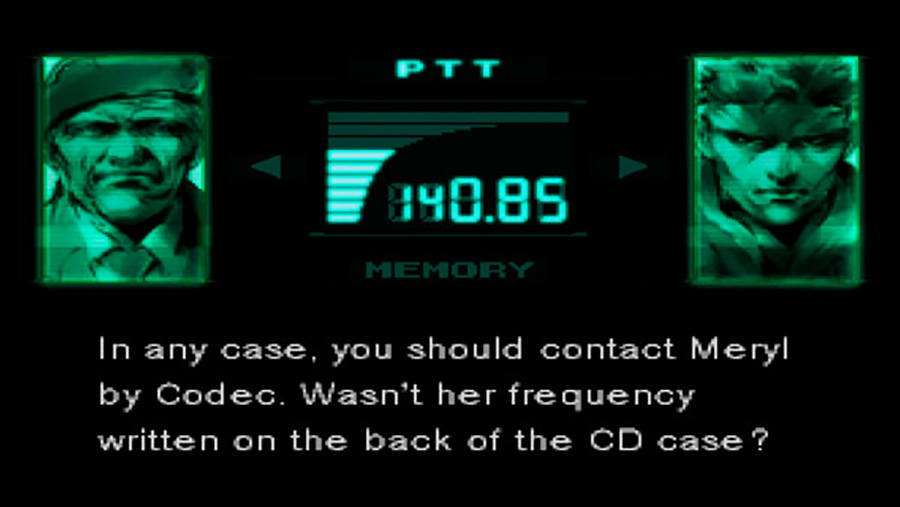 The number of the character to be called into the game is printed on the diplomatic disc box.
The number of the character to be called into the game is printed on the diplomatic disc box.
Another example is the first part of Metal Gear Solid. At some point in the game you need to call a character to change the plot. But no one will tell you where to call in the game itself, they will only hint that you need to look for the number on the game box.
Moreover, the number is on the screenshot, which is initially not paid attention to. In the re-release for modern platforms, this feature has been preserved: you need to look for the number in the manual attached to the game, in the menu (or in screenshots in the store with the game, for example on Steam).
On PCs there were also similar protection methods. One of the most famous examples is Populous, where the game periodically ordered a window with a coat of arms. The player had to open the manual, find the desired coat of arms (and there are several of them) and enter the name of the state that the coat of arms symbolizes.
But okay, here’s the manual for the game Where in the World is Carmen Sandiego? An entire book is included, information from which must be carried periodically in the dialog box to continue.
 The game came with an actual book, so you had to find the information as you went along.
The game came with an actual book, so you had to find the information as you went along.
Another problem for players was the interactive discs. For example, in the game The Secret of Monkey Island, the pirate’s face appeared on the screen, as well as the place where he was hanged. The player had to find this face by rotating the ring.
Then a code was displayed in a special window that had to be entered to continue the game. Similar methods have been used in other games with simple mechanics.
 It was impossible to complete the game without such a paper ring.
It was impossible to complete the game without such a paper ring.
This process interrupted the game, requiring you to spin the wheel several times and then transfer the information to a special field on the screen.
However, this method was abandoned due to the high cost of producing physical copies.
But there were other elements that cost even more and were more difficult to counterfeit. For example, manuals could, at least to struggle with this, be printed on special inks or on contrasting paper.
But how to copy a physical key that needed to be inserted into a computer port? Without it, a game or program (Soft protection in the same way) simply refused to work. It was simply impossible to fake this device.
 This is what the physical keys looked like, without which the games refused to launch.
This is what the physical keys looked like, without which the games refused to launch.
It was also impossible to reproduce a device called Lenslok (if the criminals are transferred – “lens-lock”). It was used as follows.
Before starting the game, an encrypted code appeared on the screen. To solve it, you had to look at the screen through a plate with a Lenslok lens and recognize the code on the monitor. After the result was shown, the game started.
 You had to actually look at the screen through the lens.
You had to actually look at the screen through the lens.
A similar method of protection was used, for example, in the Elite game. The problem is that this method involved calibrating the lenses under a certain monitor distance, and if it doesn’t have an image, you most likely wouldn’t run the game.
Sales of games with this method of protection were not very pleasing to the developers and they subsequently abandoned it.
◦ Back to contents ◬
Previously, creativity took precedence over the desires for freebies
And these are perhaps the most unusual ways to protect against pirates. In the late 90s and early 2000s, it all came down to simple license keys, disc launch, and the nasty Star Force and Denuvo. Of course, there were exceptions, for example, Serious Sam 3. If the game did not pass the fluid test, an unkillable monster would start behind the player, which would interfere with the game. However, it is worth devoting a separate material to such exceptions.
I hope you enjoyed reading. If you know another example of unusual protection against pirates that I have not talked about, write about them in the comments. Have a nice day!
Source: Iphones RU
I am a professional journalist and content creator with extensive experience writing for news websites. I currently work as an author at Gadget Onus, where I specialize in covering hot news topics. My written pieces have been published on some of the biggest media outlets around the world, including The Guardian and BBC News.










