We all somehow broke down that piracy is something, well, not so complicated at first glance. Upload the firmware somewhere, put a flash drive somewhere, oh well, as a last resort, give it to the master so that he can solder the chip.
But, as a rule, hard, soft and simple methods last for months, while a variety of changes persist. the process of “modifying” consoles. Today we’ll talk about the strangest and most frankly funny ones.
Licensed disc in the name of game theft

Let’s start, perhaps, it happened when games were stolen for one reason or another because of the developers themselves. Even if not always intentionally. For example, PSP. The most popular console of the 21st century after PS1. Why? Because it was stitched with the light hands of first savvy salespeople in stores, and then completely at home, when the hack became simpler and more stable.
History knows at least two cases when a completely free disk was used for firmware. The first is the early games of Grand Theft Auto: Liberty City Stories. A layer vulnerability in the way the game loads assets and saves file data. During this process, some background processes were also restarted.
So, if you throw a specially overloaded save into the save lock (and this can be done legally) and load this save through an early version of GTA (later they simply covered this hole, the batch with disks was recalled) – it overloaded the memory buffer and left it to get into the system. Yes, it turns out that the console broke with one of the most popular games on it.

There was also a funny way to break the firmware buffer through the first part of Medal of Honor: Heroes. There, however, saving is also necessary, and this is done through any licensed version of the game, probably even to this day. To hack, you had to open a save on your PC through the program, change the player’s name in a long list of characters (random, the main thing is that there are more than 8 of them), and then launch the game and… Edit.
At the moment of death (and never again), Medal of Honor: Heroes displays the player’s name on the screen, and if its size is increased by the limit of 8 letters set by the game, then Medal of Honor catches the buffer overload and thus opens the way to the firmware.

The only funnier story is the one with the French country Alien: Resurrection for PS1. There is a password system – everything is standard, endless ammo, level selection, and so on. However, there was one cheat code (“Left, Up, Right, Down, Right, Up, Left, Square, Triangle, Square, Triangle, L1”) that, at first glance, did literally nothing.
Its purpose will only be revealed in 2023 (the game, let me remind you, was released in 2000) – this is a debugging code that allows you to legally, even if it is not chipped, replace the disk without turning off the console. For what? To slip a blank with another game in there. The code is simple disabled the chip that is responsible for checking the license on disk.
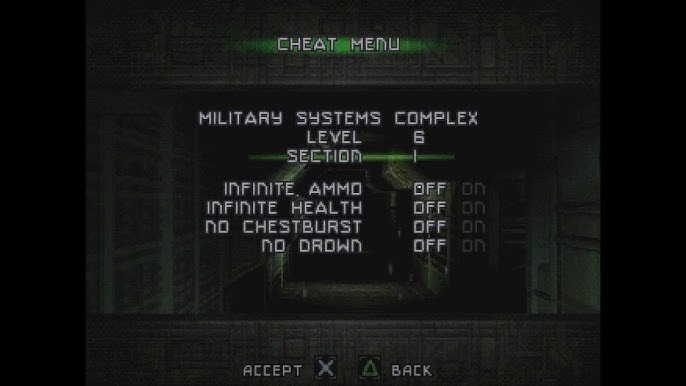

That is, how it works as an example: we go to the cheats menu, enter the code, hear a signal, go to the current level in the game, press the L1+X combination, and… the game turns off, but the console continues to work. Open the lid, remove the disk, press L1, Square and Triangle at the same time… and close the console with the disk that you pulled out. set. Even if the console no that mod chipwhich forcibly disables license verification.
And the whole comedy of the situation is that in the case of PSP exploits they were not entirely intentional and turned to console errors, but with Alien: Resurrection the situation is that this code was intentionally added by the developers. What is still unclear, but there is a theory that the team had only one set for the PlayStation girl, and in order to retreat. When updating various game builds, a way was found to disable the protection programmatically and run the builds using simple CD blanks.
Toothpicks, paper clips and other improvised materials so that any disc and game from the Internet will work

In principle, if you think about it, there is nothing wrong with the fact that one of the developers, intentionally or not, left a loophole for pirates. It’s much more interesting when people are involved in hacking or something related to it, the materials at hand are where they are, well, it didn’t seem like a place at all.
Nintendo is rightfully considered the leader of this “industry”. And if many people remember the trick with a paper clip, then, for example, not everyone knows tweezers. What kind of paper clip? It’s simple: the first revisions of the Nintendo Switch were hacked by inserting the clasp bent in the right places to the point on the case where the contact between the Joy-Con and the console passes. For what? As is clear, it seems, from the leaked specifications of the Nvidia Tegra chip – the processor has a developer mode, its activation is carried out by shorting two contacts on the board of the right slot for the joy-con.


Actually, to turn the console in the assembled state, you only needed a paper clip. However, in subsequent revisions this loophole was closed. True, this did not stop the pirates, and they found another way to put the console into defenseless mode in order to flash it.
But Switch 2 looks like an impregnable fortress, by the way. The pirates have not yet been able to find a hint how to steal games for new items.

But what about tweezers? No, the Switch can only ruin them, but for the Wii they were very useful for a while. The best-selling console of the 7th generation had full backward compatibility with the Nintendo GameCube, as well as backup ones for Old games did not interfere with operation, the console, when launching a game with “Cuba,” went into reduced performance mode through disabling several blocks of RAM.
Only here’s the thing: in order to speed up the exit from this mode, the inactive RAM blocks were not cleared, and data from the main Wii firmware was placed there. Essentially, hackers needed to find a way to transfer this information.
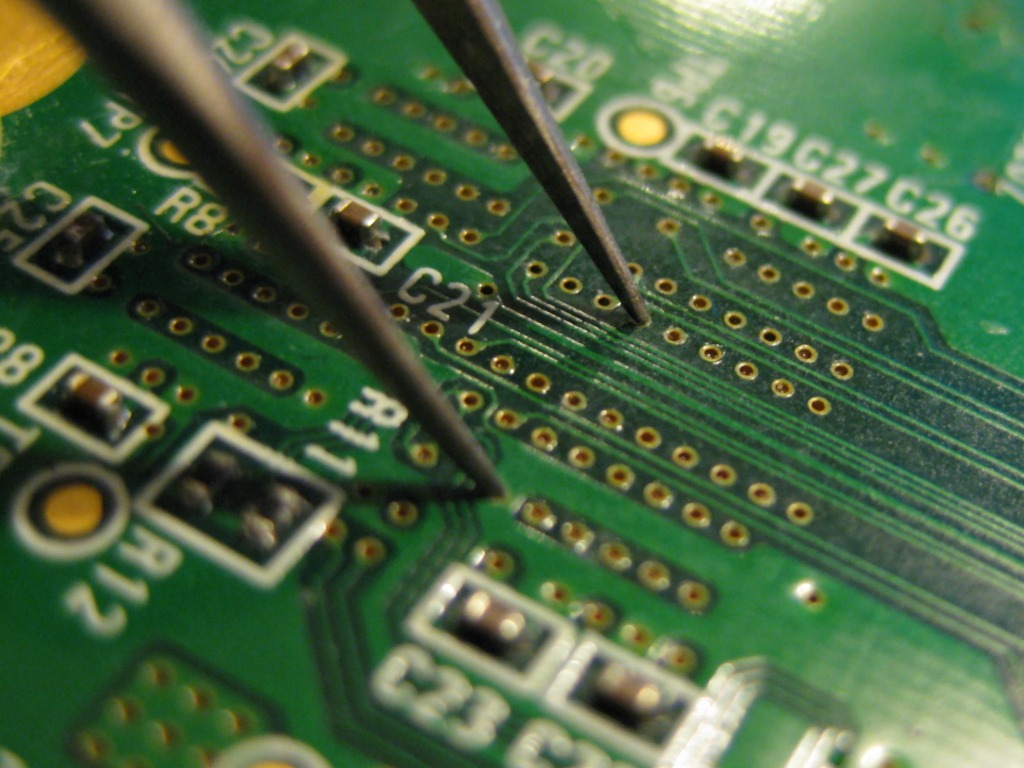
In order to do this, it was necessary to somehow activate the disabled memory areas, and this could be done using the most natural tweezers. The algorithm looked something like this: the game starts with the latest console, the Wii goes into low power mode and turns off. memory blocks, the hacker at this moment using Tweezers cover two tracks on an old board.
The short circuit “awakens”, and data from the Wii firmware (specifically, these are protection keys) is unloaded from the RAM. It is this data that allows pirates to create a full-fledged hack with which they could play hit games. for free.

The strangest method of hacking, allowing to obtain a more accurate description of the kernel firmware, was seen on the Nintendo 3DS. It was the firmware itself that was hacked using different methods, and the current method at the time of the events I described was through system overload using the game Cubic Ninja, which would load user content using QR codes, in which they put something that overloads the buffer. But it was portable and crashed when rebooting; to modify it, it was necessary to remove the console firmware kernel itself.
This was done using… a magnet. The Nintendo 3DS has one loophole for testers and developers – by pressing the Home+Select+Start buttons at the same time, it goes deep into Developer Mode and is completely open to modifying all the internal features of the software. There’s just one caveat: with the console lid open (you remember that this is a clamshell?), this is simply impossible. However, it turned out that it is very easy to deceive the sensor that is responsible for checking the status – it is located under the button. B, and if you put a magnetthe console began to think that the lid was closed (I checked it myself – the screen went blank).
Thus, with the help of a magnet, it was possible to deceive the system, take it into deep dev mode and pull out the hard firmware, which greatly simplified the method of hacking the latest portable console in the industry.
We take the Xbox 360 and drill it. Yes, after that he will launch stolen games.

But all these magnets, paper clips and disks pale in comparison to probably the most insane, barbaric and dangerous hacking method. console. It’s unknown how many people ruined their X360s when trying this trick, but its very existence is living proof that enthusiasts will stop at nothing.
As you probably remember, the Xbox 360 did not become popular even among us, because already from the first revision it not only burned (hehe), but was also quite easily flashed, causing the launch of discs with games instead of licensed discs. This was achieved through the drive firmware, and not a single Microsoft solution could save us from this. The company changed drive manufacturers several times, but the pirates played and broke the defense.
Then the company took some rather interesting measures. In the second revision of the Xbox 360, screen protection from overwriting drive data appeared. That is, it was still possible to find information for the drive’s firmware, but the recorded recorded code was no longer possible. And while one team of hackers was looking for a way to software the console, a certain enthusiast under Nick Geremia was looking for a house of the right size… a drill.


Geremia examined the drive in detail and found contacts designed for overwrite protection under the cover of one chip. Since they were not simply turned off from the software, a decision was made to allow them physically. How? Yes, very simple – take a drillwhere the contact path goes in order to open it, but not touch ANYTHING else inside the chip. It is unknown how many changes (the drives themselves) went into the debugging process, but the method turned out to be different. With the chip drilled, access to the resulting records was gained along with the ability to flash the drive.
Due to the extreme degree of extreme and the fact that there is only one attempt at everything, the method was called Kamikaze Hack. And in order to somehow minimize losses, Geremia set up small-scale mass production of special stencils for users.
The first hackers thought about DVD drive firmware to fool the disc authentication system. The x360 has a small vulnerability that is physically protected from overwriting the chip. Hacker Jeremiah came up with the Kamikaze hack. To remove the write protection, it was necessary to drill into the chip in order to break the contact that is responsible for the write protection.
They will go to great lengths to violate a subscription agreement.
In general, I believe that no enthusiasts should under any circumstances be denigrated, punished or publicly condemned. People spend hours, days and months trying to bypass protection, professionals spend years developing it, and it is highly respected.
True, now this is almost no longer the case. The same Sony consoles have been practically breaking through the browser for three generations (which is why it is not on the PS5 and Nintendo Switch, for example), the protection of the Second Switch also looks completely impregnable, and Microsoft has read entire lessons on its method of combating piracy. Who didn’t know, after the Xbox 360 no one tried or was able to hack the security of Microsoft consoles.
On the other hand, now all services are designed in such a way that, in general, you don’t really want to pirate them. There are a lot of sales everywhere, several profitable subscriptions, where there are so many games that there is not enough to go through a lifetime, and for many at our age, one big project is enough and they can slowly implement it without getting in the way. often it is even more interesting and useful than Steal official games with torrents and spend a couple of hours in each case at best.
I am voicing this thought to you. Have a good day!
2
Source: Iphones RU
I am a professional journalist and content creator with extensive experience writing for news websites. I currently work as an author at Gadget Onus, where I specialize in covering hot news topics. My written pieces have been published on some of the biggest media outlets around the world, including The Guardian and BBC News.










