The day before yesterday, insider @analyst941 deleted his Twitter account, confirming that he was forced to do so by Apple.
The company figured out his sister, who leaked information, and then fired her after another insider tweet. Against the backdrop of this story, 9to5Mac decided to tell how Apple is struggling with information releases.
The company has a lot of means to ensure the safety of sensitive data.
Apple culture of secrecy

In most tech companies, secrecy is a propensity for competitor allergies. If they notice or suspect that other companies are working on the same idea as them, such organizations come first to market. Accordingly, I would not want anyone else to know about their plans or how close they are to launch.
However, with Apple, the situation is different. The company is rarely seen on the market. Instead, she watches and waits until her products are published. Apple is the best, not the first.
However, in Cupertino, their own secrets are still being implemented. It has to do with Steve Jobs’ thinking that sudden announcements are magic. It is this desire for magic that surprises with Apple’s heightened level of secrecy.
How Apple reveals its secrets

The company uses a large number of leak protection methods.
For example, Apple has a disparate product development system. The bottom line is that including small groups of people who are working on withdrawing the product are detected or detected, while other groups about the inclusion of others are not detected even in a number of cases.
Apple. In some cases, employees don’t even know what product category they’re working on. For example, they produce audio technology, not even foreign, whether it will be in Russia in HomePod, Mac, AirPods or iPhone.
Prototypes are very accurately camouflaged if they are to be used in application areas. They are followed very often. This is a lesson Apple learned from its own bitter experience after its infamous use with an iPhone 4 prototype that was left in a bar.
Apple tracks both network activity and the use of natural things like USB keys.
The company also warns employees that disclosure of information is a criminal offense and that the company may even seek financial damages from them.
However, some employees are leaking information, and even with scattered secrets, Apple believes that this can lead to an increase in the number of people. However, the Cupertinites have special methods for calculating “drainers”.
How Apple calculates “rats”

With Apple focusing on product design, it’s no surprise that the company is especially hard at work rejecting visual material leaks: product images, blueprints, CAD images, and images.
Here are just a few of the methods Apple uses to deal with leaks.
• invisible watermarks
Everyone is familiar with the usual watermarks – they appear on the visible part of the image to show authorship. There are so-called invisible watermarks.
This square appeared black:
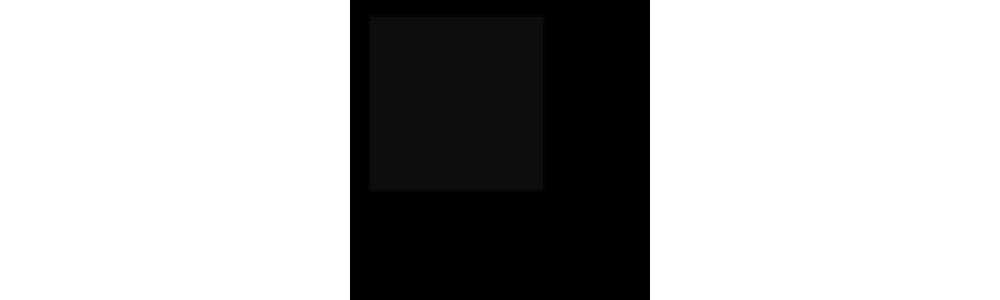
In fact, one part of it is #0D0D0D instead of #000000. By making these changes to different pixels, you can create an almost infinite number of variations that don’t show up.
We used black as an example, but the same can, of course, be done literally in the entirety of the image.
This is why we never share real images provided by sources. We always repeat them, and they never come out as this copy of the original.
• file name
Another reason why Apple used anonymous filenames, like this:
🔺 very_secret_image_46793459583203.jpg
🔺 very_secret_image_46793469583203.jpg
• serial numbers
Document serial numbers are another way to evaluate insiders. For example, when Apple plays a walk-out video, each video is watermarked with a foreign number, which is likely an Apple Connect worker ID.
• barely noticeable font change
With a serif font, a particular version of text can be created with a pixel missing by one stroke in one instance of one letter. Font sizes can also be increased or decreased by just one pixel.
• explicit font changes
Sometimes Apple takes the opposite approach and opts for very obvious changes. If they want employees to know their copy is being tracked, the company uses random rates or bold fonts.
For example:
This year iPhone 15 will be launched on Tueornik 29 august vmeuthen the usual septemberwhom time.
• changes in wording and punctuation
In some cases, Apple makes small changes to the texts. Often they send ready-made text, so it will not be difficult to calculate the source.
For example, what the original text might look like:
This year, the iPhone 15 will launch on Tuesday, August 29, instead of the usual September time.
Or like this:
This year, the iPhone 15 will launch on Tuesday, August 29, instead of the usual September time.
Or like this:
This year, the iPhone 15 will launch on Tuesday, August 29, instead of the usual September time.
In all cases, wording or punctuation is expressed, which can be easily missed when forwarding to other people.
• fake information
There are ways to deal with the “co-owners” of information. Obviously, this took place, the corresponding employee is not working.
For example, for personnel doing work that does not allow distribution with radio bands, pre-post how easy it would be to change one digit in this table (they would not even notice the catch):

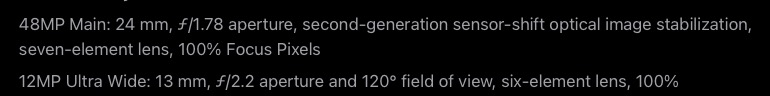
Or vice versa. For someone who works with radio bands, drop the text that says f/1.76 instead of f/1.78:
There are plenty of options. It is possible to “leak” non-collective information, including model numbers, colors, fake representations, and more.
Did @analyst941 really have any information
We can’t know for sure right now. Closer to the point, let’s check which of his incidents were true. [9to5]
Source: Iphones RU
I am a professional journalist and content creator with extensive experience writing for news websites. I currently work as an author at Gadget Onus, where I specialize in covering hot news topics. My written pieces have been published on some of the biggest media outlets around the world, including The Guardian and BBC News.










