Contrary to what you might think, the fact that a stranger has access to your modem can give them an advantage in accessing your and your family’s personal information, as well as access to security cameras, for example. Buthow to find out if your phone has been stolen WiFi? Below we will show you some simple steps to protect yourself in most cases.
You might be interested in:
- What is an unhackable quantum internet?
- What is the Internet of Things? All about the Internet of Things
- How to remain anonymous on the Internet
Of course, the goal is to ensure that no unauthorized device connects to your personal Wi-Fi network, both because of the performance issues it entails and the security threat it poses. In short: If something strange is happening with your connection, it’s important to check and resolve the problem as soon as possible (and remove the rogue pest from your network in the process).
Is someone stealing your Wi-Fi?
If you only have a few Wi-Fi devices in your home, you can unplug or turn them off and then check the wireless signal light on your router. If the light continues to blink, it may mean that someone else is using your Wi-Fi.
However, this method only works if you are sure that all your existing wireless devices are turned off, which can be difficult in many homes. Therefore, we present two detailed methods to check whether you should worry about Wi-Fi thieves, regardless of your configuration.
Method 1: Use an app.
There are many apps available to automatically search for unusual devices registered to your Wi-Fi network. Testing these devices, especially if they come online at odd times of day, can provide valuable information. Here are some apps that can help you identify problems.
Wi-Fi thief detector: This app is easy to download and is designed to give you quick results. It will show you how many devices are connected to your router, help you detect strange devices, and link you to settings to quickly make any changes you need.
Paessler PRTG router monitoring: Paessler’s solution provides a complete set of router management tools, including automatic rogue traffic detection, network usage analysis, and other detailed tools.
This may be a little extreme for the average homeowner worried about their neighbors, but it’s a great tool for small businesses worried about someone being on their network without permission. We suggest you opt for a 30-day free trial, which should be enough to troubleshoot any issues.
Wifi guard: Available for iOS and Android, this handy app has a nice, minimalistic interface that allows you to scan all the devices on your network and look for anything suspicious. You can view details of any suspicious devices and receive notifications about any new devices that have just entered your network.
Wireless Network Watcher: This standalone software is designed to help Windows and MacOS users detect suspicious wireless activity and monitor all devices connected to their network. It’s similar to Wi-Fi Inspector, but has wider compatibility if you don’t want to use the Google app.
Fing: is an iOS download that provides more mobile protection. This allows you to see at a glance the connected devices, their type, connection nature or MAC address, among other things. You can also check your connection behavior to account for particularly busy periods, which may indicate someone else is connecting to your network.
Method 2: Check the admin logs.
If you suspect someone is stealing your Wi-Fi, you should log into your router’s management page. Most systems can do this by typing “192.168.1.1” or “192.168.2.1” into the browser’s address bar. If that doesn’t work, check out our guide on how to find out our router’s IP.
Once you have accessed the administration page, you need to find a page that lists the various media access control (MAC) addresses connected to your computer. The location of this page varies by router, but you may find it in the “Wireless Settings”, “Wireless Status” or in the “DHCP Clients” list.
You can use this list to count how many devices are connected to your internet. If you see more MAC addresses than the number of devices in your home, someone is probably stealing your signal.
Note– Old cell phones, game consoles, Wi-Fi enabled cameras, and other connected devices may appear in the MAC address list. You can have more control over which MAC address represents which device by using a website like macvendors.com.
How to protect yourself from internet thieves

If you suspect someone is stealing your Wi-Fi, it’s a good idea to tighten up your security initially. If you don’t have a password on your network, be sure to add one. If you are still using the default name and password of the router you purchased, you should change them, and you can easily do this from the router’s management page. Below we will explain how to do this.
To change your password, find the key in your security settings. Keep in mind that changing your wireless password will disable all of your current devices (including thieves), so you’ll have to reconnect all of your devices once you have the new password.
To change your router name, find Service Set ID. This is usually found in the wireless settings menu. Once this is done, you can change the name of your router.
Finally, it is important to use the strongest wireless encryption and encryption you can find, currently this is WPA2, but WPA3 is much stronger, although it is not yet supported by many routers.
If your router was made before 2006, it may not support WPA2 encryption. In this case, we suggest you buy a new router to ensure that no one steals your internet signal.
Remove strangers from your Wi-Fi
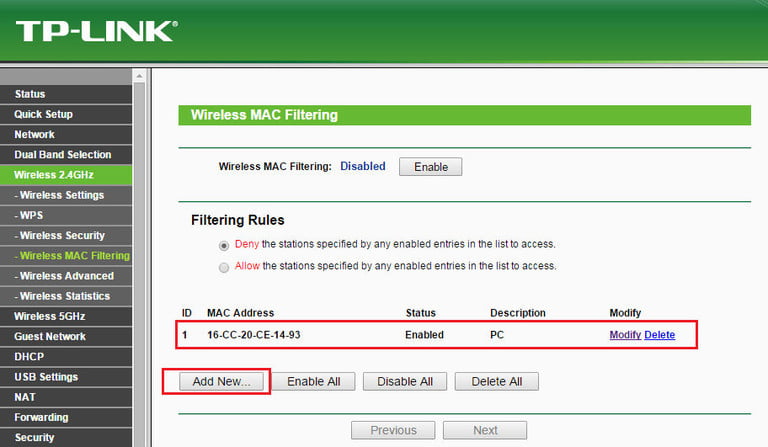
So far so good, but what if you find a stranger on your Wi-Fi and want to get rid of him? The easiest and fastest way is to change the WPA2 password to a more complex one. This will remove all devices from the network, allowing you to log in again and preventing anyone who doesn’t have the password from logging in. This should be enough to deter casual thieves from making future attempts, although you should monitor connected devices frequently.
Another option is to look for an alternative on your router’s admin page that says MAC filtering, Device filtering or something similar. This way you can add MAC numbers to the list of blocked devices. Select strange MAC numbers of unknown devices and add them to this list. This is not a foolproof solution as MAC addresses can be spoofed, but this would be quite unusual on home networks.
Source: Digital Trends













