It’s the holiday season, which means an onslaught of scammers trying to lure digital shoppers into their fraudulent networks. Even Google had to issue a warning about celebrity scams, fake account scams, and digital extortion. Of course, Big G took the opportunity to extol the virtues of the company’s anti-spam techniques. Gmail.
The government, however, takes the threats very seriously, extending to the realm of sophisticated cyberattacks and telecommunications breaches targeting high-ranking officials and senior politicians. To this end, the Cybersecurity and Infrastructure Security Agency (CISA) has released a set of recommendations for protecting smartphones.
Recommended Videos
This is the best part. You, the average smartphone user, can (and should) try to follow as many of these agency security tips as possible. We’re talking about advice from the guys at an agency overseen by the Department of Homeland Security (DHS), so you better pay some attention.
Messaging Security Tips
Let’s start with messaging. CISA’s first general communication advice is to use end-to-end encryption services. Right now the default iPhone iMessage pipeline and protocol RKS Google recommends using the Android Messages app with end-to-end encryption.
If you live in an area where these two factors are not the norm, use platforms like WhatsApp or Signal. You can also enable end-to-end encrypted chats for Facebook, Instagram private messages, and Telegram, and we highly recommend you make the extra effort here.
2FA and access codes
The next line of defense is to enable hardware or hardware authentication to verify identity. The ecosystem built around Google and Apple now offers support for Passkey, and they are now also linked to their respective Gmail and Apple IDs.
Activate them if carrying a physical FIDO hardware key, such as one from Yubico, seems like too much of a hassle. Google’s Advanced Protection Program (APP) and Apple solutions like Private Relay are just some of the other existing features you should take advantage of.
Another important suggestion from CISA is that you should get rid of SMS-based multi-factor authentication as they are susceptible to different types of attacks. Switch to authentication apps instead. Authy is a great option, but if you want to stay in the software ecosystem, Google and Microsoft also offer their own authentication apps.
Use a password manager
If an authenticator app doesn’t suit your workflow or productivity, rely on a password manager app instead of the inconvenient (and hack-prone) method of remembering dozens of passwords. We have a verified list of the best password manager apps.
Google Password Manager is a great option for in-house development, and Apple recently released its own pretty excellent password app. There are also many third-party options, such as LastPass and 1Password.
Of course, digital hygiene starts with a strong password. And no, we’re not talking about the ever-popular and easy-to-guess options like ABCD1234. Select an alphanumeric combination and add some symbols, as well as upper and lower case letters.
The Value of a VPN

Additionally, if you live in a country where carrier accounts form the basis of your mobile data usage, set a strong password for that SIM account. If you think spying is a problem (which is a widespread grim reality), use a VPN to surf the web.
If possible, pay for one instead of using the free VPN route. Nothing good is free, and if it is free, it comes with a hidden price. In this case, it’s your digital identity and your privacy. Don’t know where to start? Digital Trends experts thoroughly tested best VPN services so you can make an informed decision.
Some final safety tips
Of course, safety starts at home. In this context, we are talking about the computer that is always with you: the humble smartphone. iPhones allow you to disable sending messages using the insecure SMS protocol if the data is not available. Go ahead and follow this path: Settings > Applications > Messages > Send as text message.
Next, go to the privacy and security panel in the Settings app, review the permissions apps are granted access to, and perform a cleanup. The designer calculator app does not need to know your location or have access to embedded files. In this guide, we have detailed steps to control your app permissions for both Android and iOS.
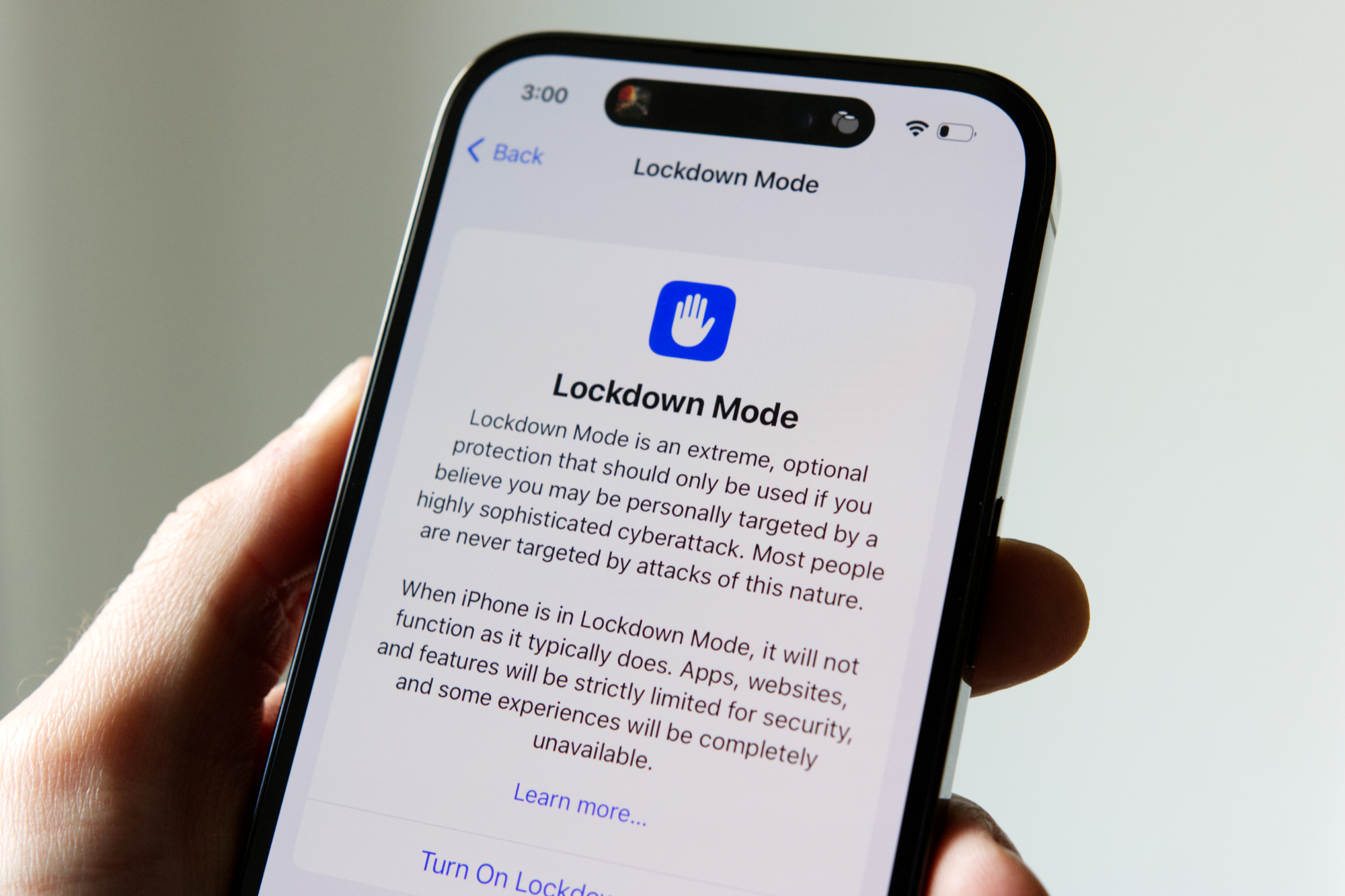
If you detect malware activity on your iPhone, activate lock mode and contact law enforcement. We have a detailed guide to help you understand the pros and cons of this feature.
Google, for its part, offers a security dashboard for all connected devices. I highly recommend that you spend a few minutes clicking the switches and clearing the security warnings.
It’s impossible to be 100% secure online or on your smartphone, but if you take the time to follow a few tips, you can significantly reduce your risks. Be safe there!
Source: Digital Trends