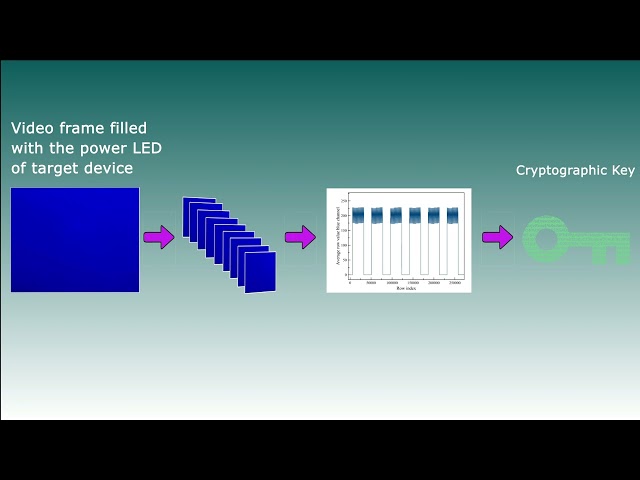
The verification teams at Cornell University and Ben-Gurion University have developed new packages for various malicious gadgets and information systems protected by cryptography. The method is very effective and is based on a subtle analysis of the glow … of a conventional LED. Scientific research concerns the fact that any manipulation of data is made with changes in consumption. This causes the computer unit’s power indicator to be configured, which can be configured as a channel for hacker attacks.
There are also sound patterns or electromagnetic field changes in this game. I also watched a video of the power indicator, which was visible to us from the street, a smart cart recorded at a distance of 16 meters by an embedded IP camera, managed to recover a complex 256-bit encryption key. In another experience, the power indicator of speakers connected together with a smartphone to the same hub gave enough data to disable the 378-bit key of the Samsung Galaxy 8 key.
In the right hands, this technology can become a real weapon. The danger is that only a smartphone is enough for hacking, and the attack itself can be completely invisible to others. In addition, hacking can be successful even if the hackers are at a sufficient distance from the device being armed.
Source: Tech Cult
I am a professional journalist and content creator with extensive experience writing for news websites. I currently work as an author at Gadget Onus, where I specialize in covering hot news topics. My written pieces have been published on some of the biggest media outlets around the world, including The Guardian and BBC News.












