When a new vulnerability is discovered, Criminals discover this in less than two days. In the latest security company Sonicwall Survey, 61% of the gaps are used in cyberliks within 48 hours after determining.
These data are a part of the Annual report that analyzes cyber security models and deals with the frequency and volume of attacks on the effectiveness of the defenses and repairing systems.
According to Sonicwall, Approximately 17.84% of the discovered violations are investigated in less than one day.. This number rises to 42.89% for the security deficits used within two days after the public is opened.
“Analysis of the exploited main security vulnerabilities shows that the attacks occur in less than 48 hours than the publication of the concept evidence (or POC).” Sonicwall says. “This tendency was strengthened by Google Threat Analysis Group, which states that most gaps were investigated in less than two days before they were published.”
According to the company, these attacks are often aimed at the Microsoft Exchange corporate platform. The process has become even more accessible due to the growth of the existence of devices designed to provide cyber attacks and the growth of the ransom software-fridge (RAAS) market.
Raas would be like renting ransom software: cyber criminal X renters malware (viruses) developed by a cyber criminal for a predetermined period to infeculate other systems.
Sonicwall Research strengthens the importance of keeping updated systems, implementation of defense mechanisms, and especially constantly monitoring new threats in the institutional context.
Viruses spread through HTML and PDFs
Sonicwall’s survey, 38% of the analyzed malicious files were compiled in HTML/PHP codesIt is common in web documents. Latter, PDFs representing 22% of infected packages appear.
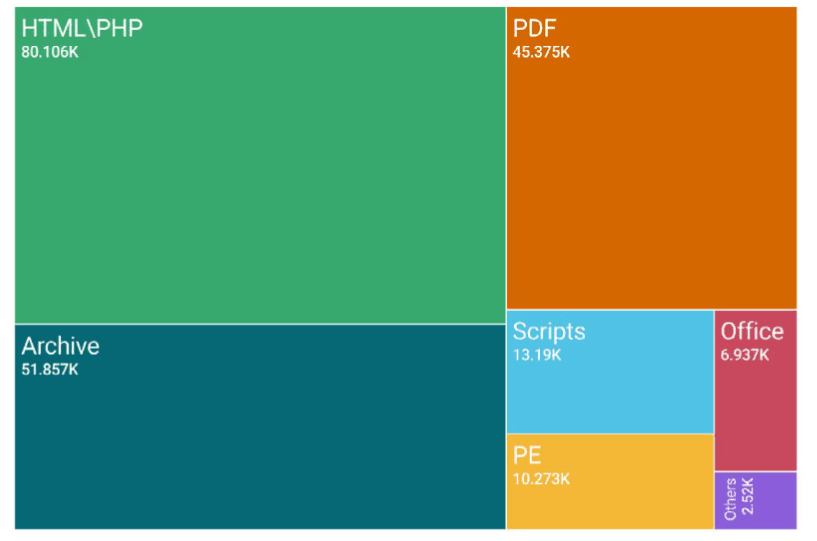
“Strikes use these formats because they make it easier to improve safety systems by discovering human behavior to steal precise information, such as identity information,” Sonicwall says. “Criminals direct victims to identity hunting areas through QR codes placed in malicious PDFs. When scanning the code, the victim is seemingly taken to a legitimate entry page, but designed to capture and guide his knowledge to the strikers. Konuş
Ransom software attacks are growing in Latin America
Sonicwall’s report also points out that ransom software attacks have grown by 8% in North America, but are fired in Latin America. Increasing 259% in 2024. The main target is health network systems.
Last year, more than 198 million Americans were influenced by cyber attacks. One of the biggest events was the occupation of the Medical Aid Company systems systems in February 2024, which resulted in a major exposure of data from 190 million people, including contact information, health plans, diagnoses and payment data.
Only in 2024, More than 210,000 malware “never seen before” malicious software has been detectedEquivalent to approximately 637 new threats per day.
Malicious android applications become a problem
Finally, Sonicwall says that malicious applications for Android have become a growing threat, especially in the Asian-Pacific region. Criminals benefit from the wide popularity of Android devices and the confidence of users in authority figures to play data.
“These applications usually enter legitimate financial or government services. When we combine this with the lowest digital literacy in some regions, it is clear why some groups are more vulnerable to such attacks, Son says Sonicwall.
Source: Tec Mundo
I am a passionate and hardworking journalist with an eye for detail. I specialize in the field of news reporting, and have been writing for Gadget Onus, a renowned online news site, since 2019. As the author of their Hot News section, I’m proud to be at the forefront of today’s headlines and current affairs.










