For most of you, a large amount does not fall into the hands of gadgets, but the information stored on them. Cupertino are doing everything possible to increase the level of its security within the Apple ecosystem.
However, we often use other people’s services, other people’s computers and sensitive services, which leads to increased risks.
To the point: Like an iPhone owner. We prohibit access to applications for photos, GPS and more
Currently accepted and implemented, which evaluate the accounting of your data. Everything is configured in a few minutes, and the work of hackers and password pickers is done for several weeks.
1. Change the structure of passwords
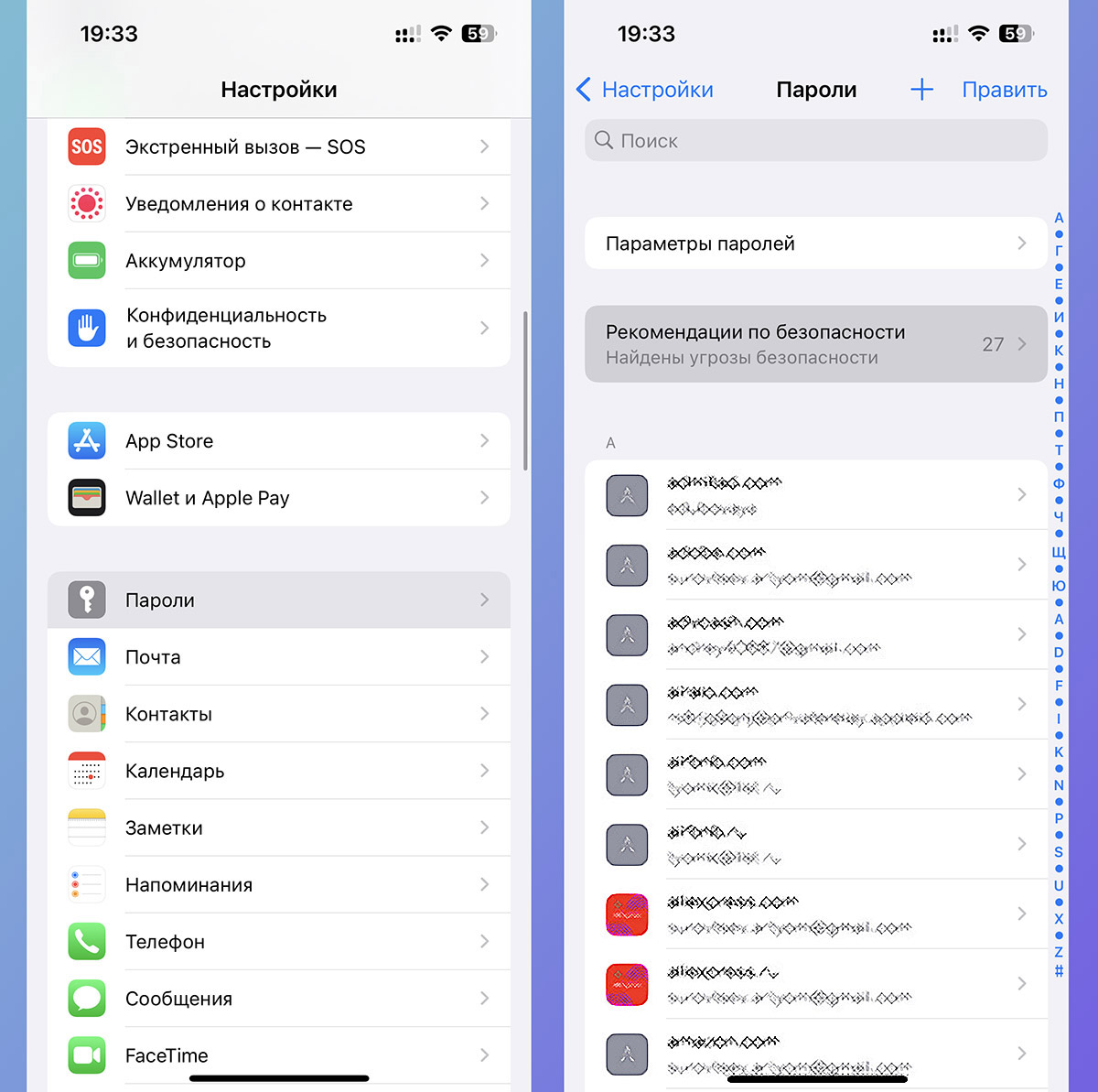
Apple’s mobile OS has long had a built-in record system for changing passwords. Starting with iOS 14, the device must use passwords and leaked data from your keychain.
It is necessary to draw up official recommendations and independently change weakly protected authorization codes.
What to do: ease Settings – Passwords – Security Recommendations and change all combinations or compromised passwords one by one.
You won’t be able to clear the entire list right away, but gradually, in several approaches, you will be able to use your credentials on different sites.
2. Turn on two-factor authentication
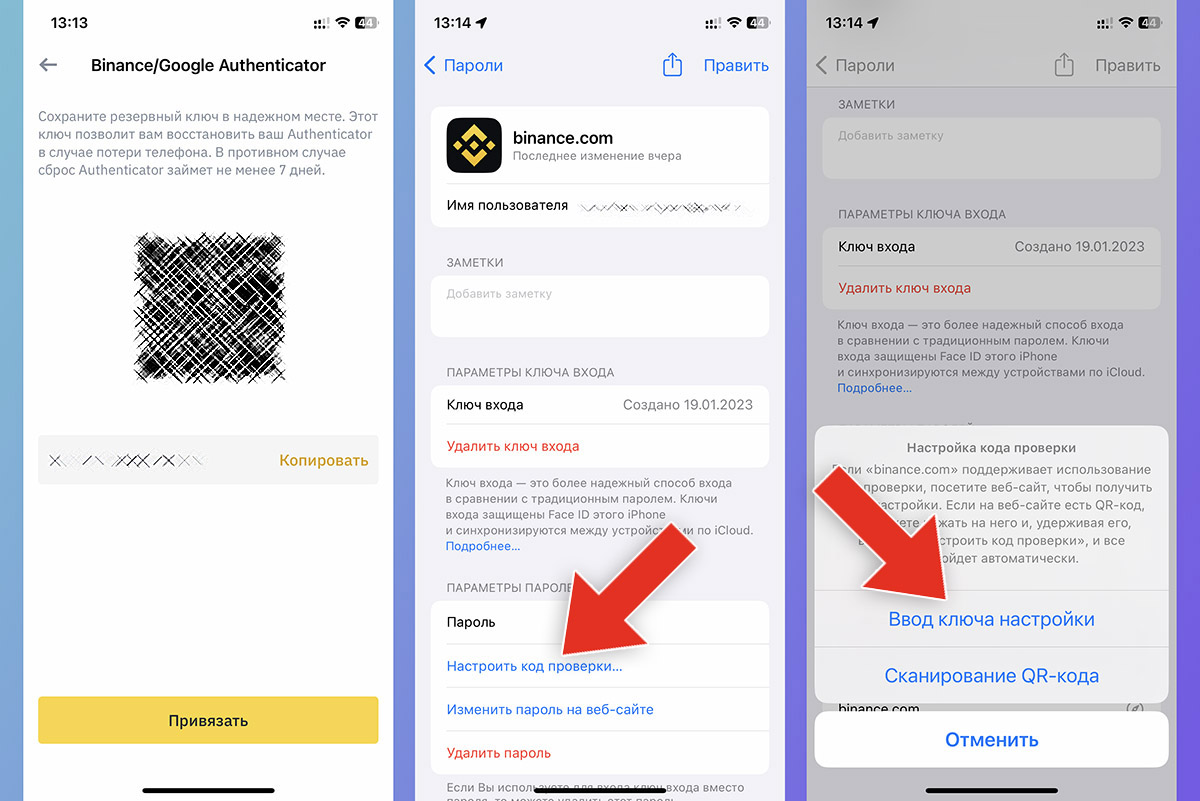
An additional factor for verifying entry into an Apple account has existed for a long time; a similar verification can be activated in most popular services, social networks, mailers and instant messengers.
In the beginning with iOS 15, the verification code can be received not by SMS or email, but directly in the distribution system settings.
What to do: added authorization check through iPhone settings. So, for example, you can quickly resolve the operation on the crypto exchange Binance.
3. Use cross-platform password managers
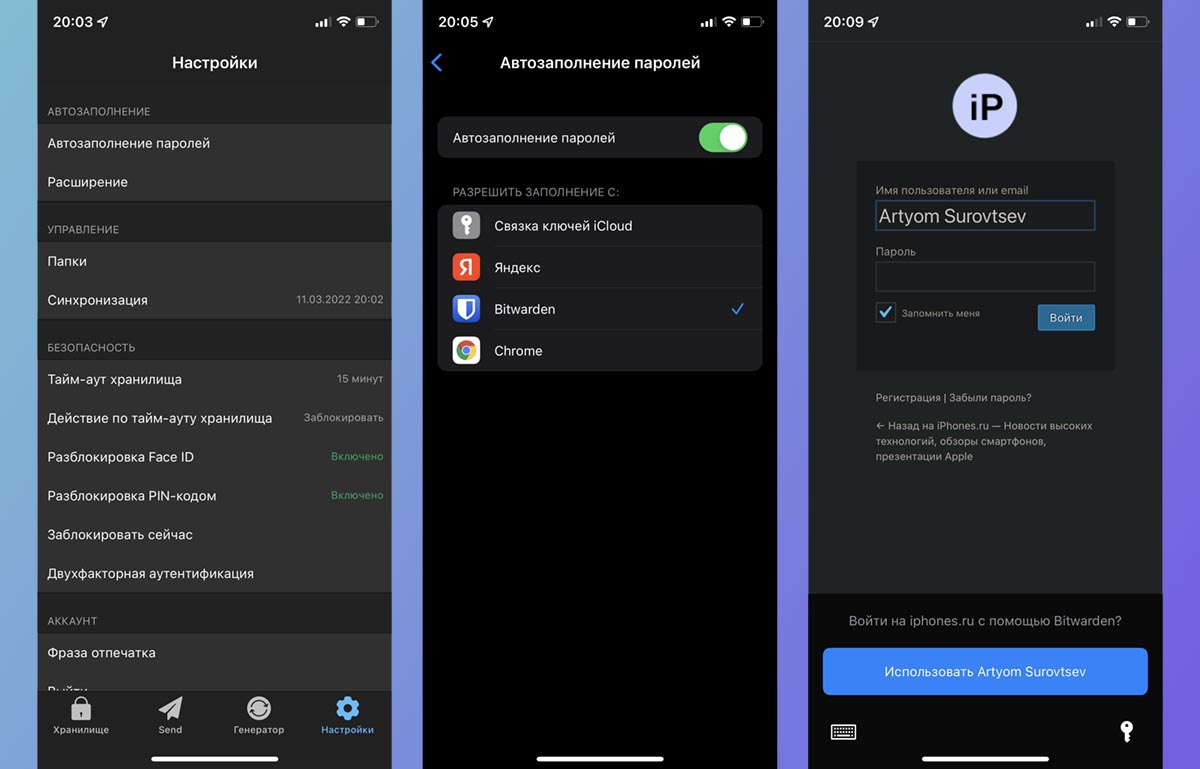
If you work with ecosystem accounts outside of Apple, be sure to set up a cross-platform password manager. Many people find it necessary to simply copy the codes through the messenger when they need to log in to their account on a computer with a Windows PC or Android smartphone.
Passwords request settings in the cache or are intercepted by third-party applications.
Problems can be solved using applications that work on any computer or smartphone. All passwords from the associated keys can not necessarily be saved, but the data from the main accounts, mail and social networks can be saved.
What to do: install an external password manager, e.g. free Bitvorden and transfer data according to our instructions.
4. Get Shore Protection Keys
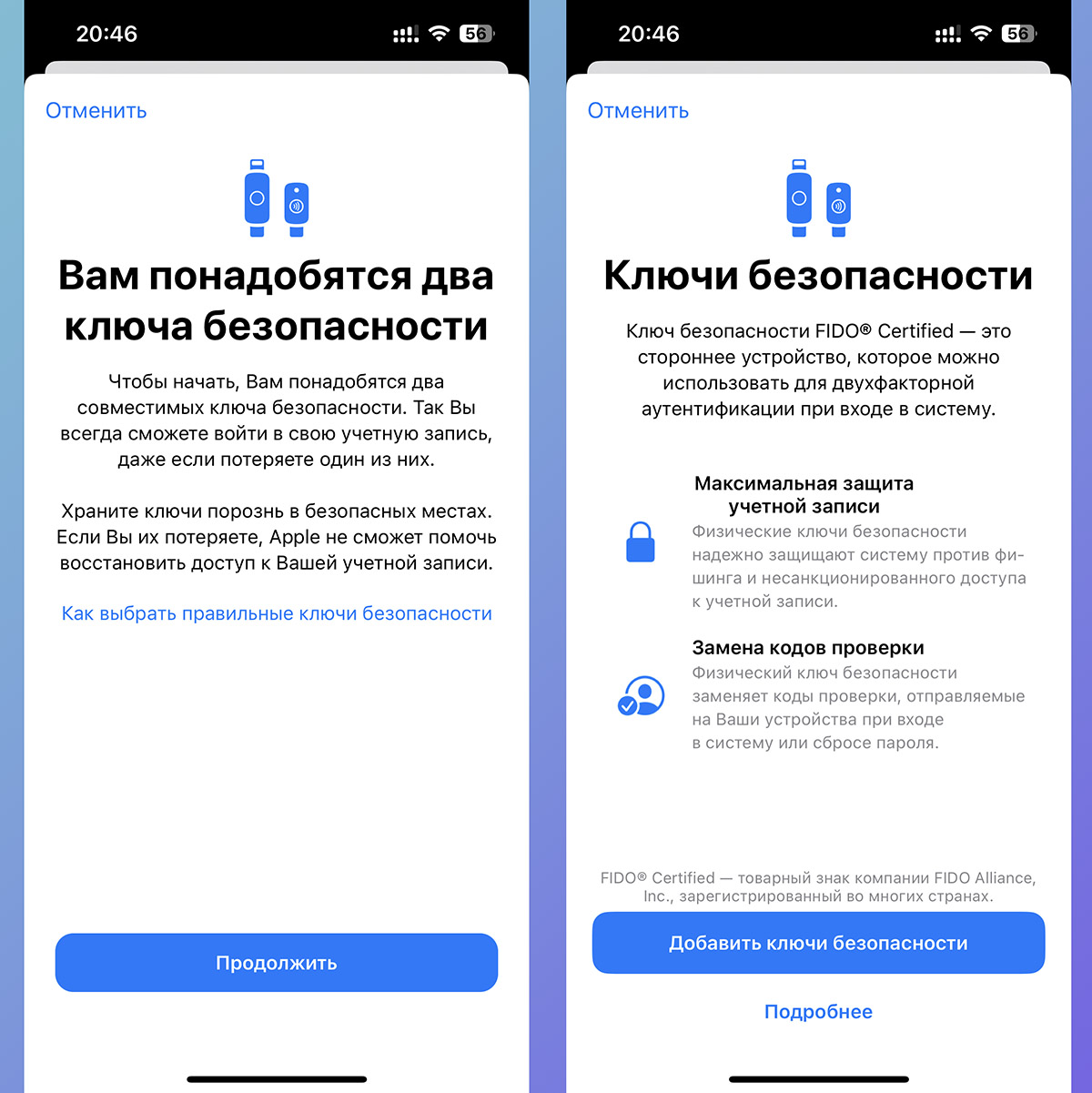
A much broader possibility of using your own accounts is authorization through individual triggering. Support for FIDO keys appeared at the system level in iOS 16.3.
You can use from 2 (one key cannot be added) to 6 keys with proper standard support and use them as a second use when authorizing on sites and services. When the system asks for additional verification, you need to attach the Connected Key to the NFC module of the iPhone.
When playing with computers or tablets with a port connection key Type-C or USB-A. Such accessories are not cheap, for a pair of NFC-enabled keys they pay 15-20 thousand.
What to do: get a pair of keys with certification FIDOset them up in the menu Apple ID – Password & Security – Security Keys and follow the federal settings wizard.
The key is then subsequently added as a means of authentication to all available sites and services.
5. Turn on iCloud Advanced Data Protection
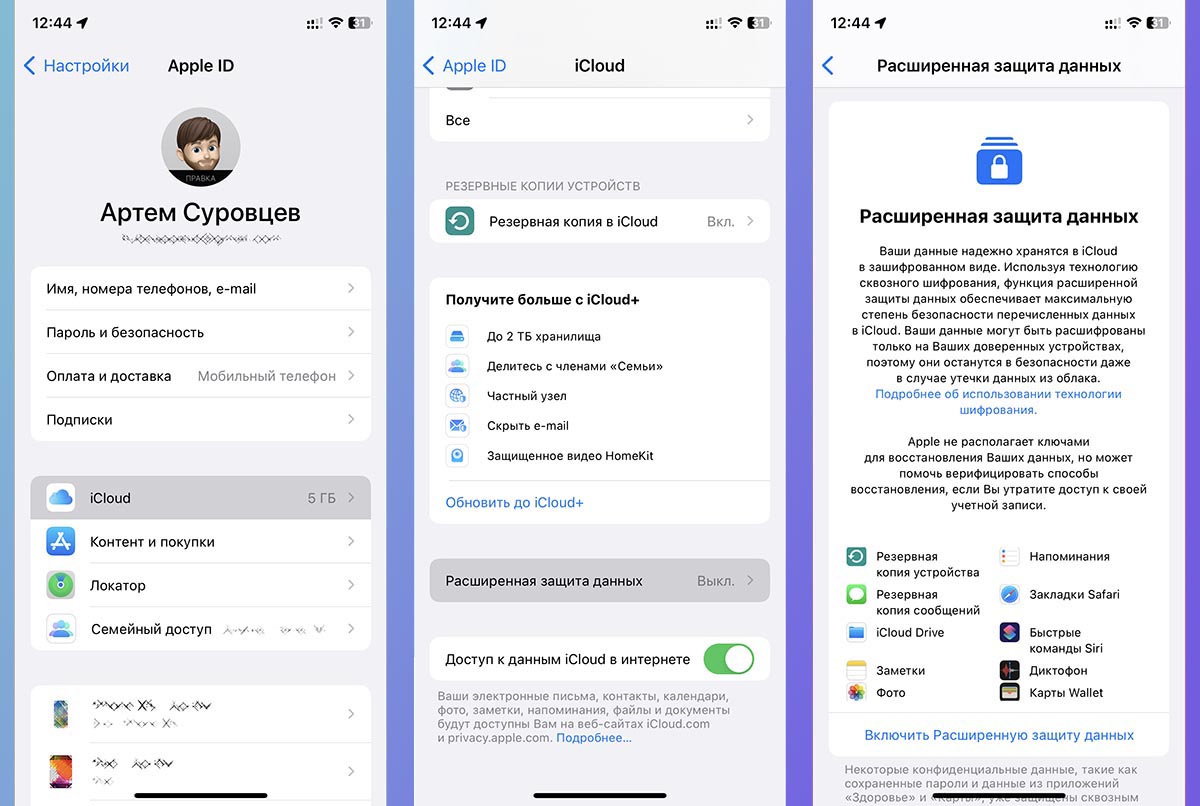
End-to-end data encryption allows you to receive information from theft on the network. Files and documents will not be transferred as an Apple set-top box. For now, this only applies to standard iOS and macOS apps. Most likely, in anticipation of the renewal of the program.
Now you can set up encryption if all gadgets have the latest software version installed.
What to do: ease Settings – Apple ID Account – iCloud and activate observables Advanced data protection.
6. Set up advanced account recovery options
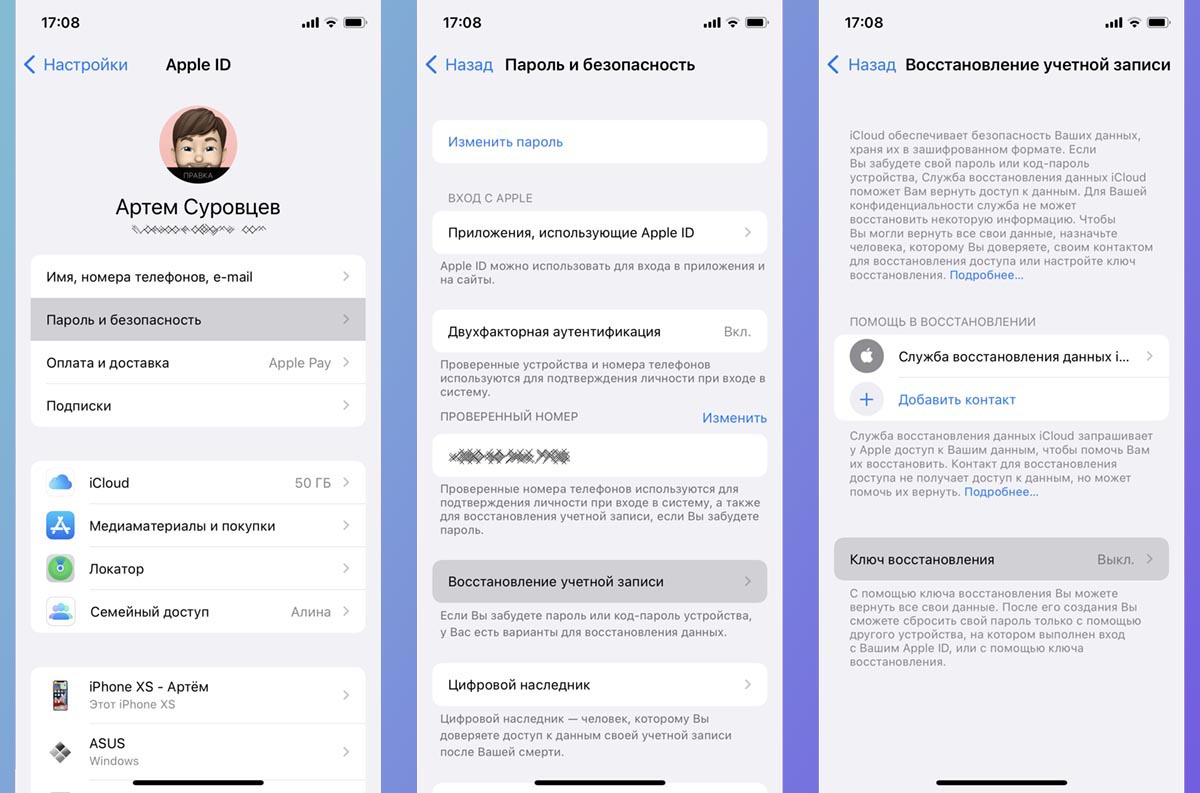
You may need this if you lose your password or gain access to your Apple ID (and with it, to A bunch of keys). Doesn’t go through a long agonizing rehab through the support of support that one of Apple’s ecosystem options can offer.
▶ trusted contact – select a friend or relative with your Apple ID account, to which, in case of danger, the unlock code for your account will be sent.
▶ recovery key – your code will be applied with which you can access a blocked Apple ID entry. Take care of the storage and protection of his weapons yourself.
What to do: you need in the Apple ID settings in iOS and one of the chips according to our instructions.
If you do at least a few of the tips from the list, it will make it much more difficult for hackers and scammers to hack into your accounts above.
Source: Iphones RU
I am a professional journalist and content creator with extensive experience writing for news websites. I currently work as an author at Gadget Onus, where I specialize in covering hot news topics. My written pieces have been published on some of the biggest media outlets around the world, including The Guardian and BBC News.