Pay attention to this new North Korean malware for MacOS made with a video call from a popular application
The new security research reveals the functioning of a malware of North Korean origin, works with telegraph and sends a wrong zoom e -mail, “Nimdoor” works in this way
According to an investigation published by computer security experts, Sentinellabs, A new malware emerged by North Korean hackers and what to talk about being More sophisticated than common malware initiatives. Threatening Combine C ++, NIM and Applescript to remain active in committed systems. The worst is that it is attentive to a large industry like crypto currencies and works using the wrong video call invitations.
“Nimdoor”, the malware formed by North Koreans, occupying using zoom
The investigation shows that the attack is directed to crypto currency companies, private web and crypto case. They use NIM’s “compiled duo” and the attacks multiple. In MacOS, they threaten the “injection of processes through WSS and the remote communication process”. They continue to attack and managed to keep it in the apple text, helps them to have the first access and reinforce In a way that will function as the back door. Keychain ID information, browser data, and even telegraph user databases can even play.
How does it really work? The victim is contacted with telegram that is passed through an additional contact. A video interview was programmed and the connection (violated and wrong) was sent by e -mail It simulates as the “wrong update of Zoom SDK”. What these North Korean attackers do inside is to hide the function with more than 10,000 white space lines.

Part of the starting software starting with an input anchor
When the malware manages to leak after opening the alleged SDK, the execution starts with a encrypted connection with a server that seizes control.. It is so powerful that the infected system has a support if the restarting or finishes are restored to the original software. You can see the detailed report of the operation here.
A strong malware, a simple way to protect you
Since we have seen a few malicious cases in iPadizate, there is a peaceful and effective solution to avoid falling into it. Remember that Phishs, a wrong E -Posta that shows that everything is real and invites you to click on unknown connections, is done through the known attempt. Before opening an E -Post, be sure to be about a frequent sender or that you are familiar for post -receipt.. If you think there is a spam e -mail, send it to the corresponding folder and then remove it.
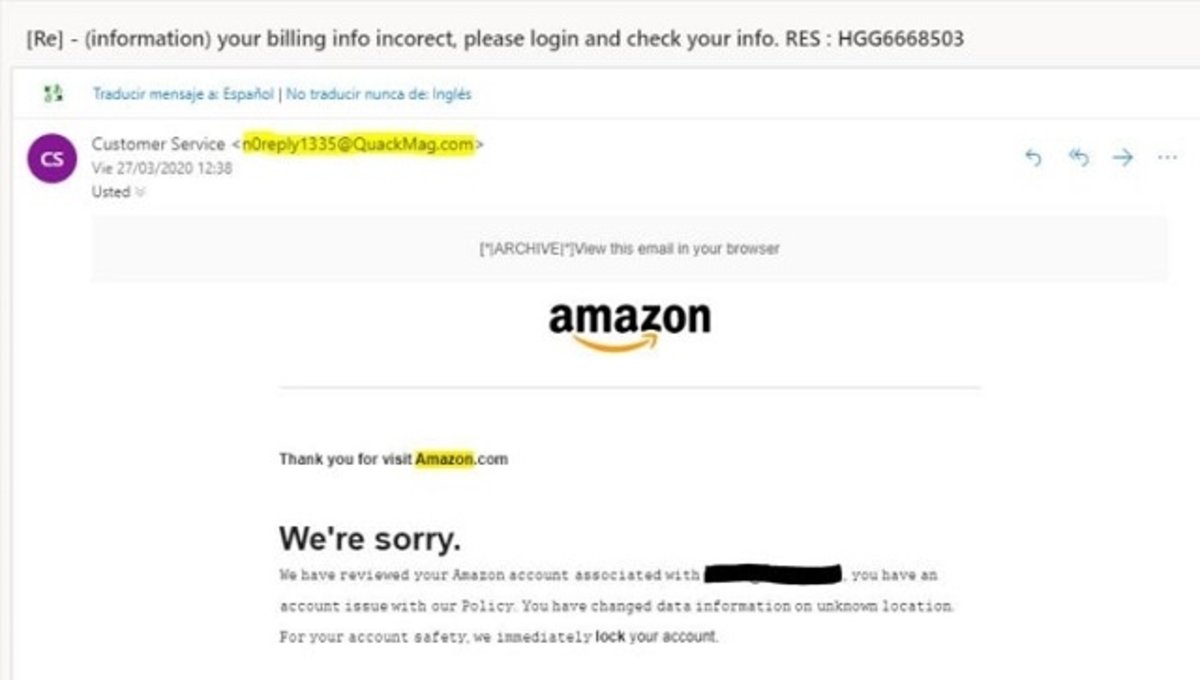
Identity Hunting Trial that uses Amazon as a shield
Yes Open an E -Post that you think may be a deception or identity hunting attempt, just read the name of the sender with the name of the mail and with the domain name. The first example is to determine if there is a fraud. The most important thing is not to click on any link. Consider your E -mail next time.
You can follow iPadizat Whatsapp on Facebook, Twitter (x) Or consult our Telegram channel to be up -to -date with the latest technology news.
Source: i Padizate













