To be careful! This malware can steal your iCloud passwords, files and bank details
MacStealer is the latest detected threat for Mac!
Although Apple rightly prides itself on the security of its operating systems, it is inevitable that cybercriminals will occasionally insist on exploiting a vulnerability to attack. According to a report shared by security researchers at Uptycs**, a new piece of malware named MacStealer has been detected targeting Macs.**
MacStealer is designed like this: extract iCloud passwordsespecially those related to our financial data, for example Passwords, cookies and credit card data from Firefox, Google Chrome and Microsoft Brave browsers. The report states that it can extract several different file types, including .txt, .doc, .jpg, and .zip, and the Mac password manager database KeyChain.
MacStealer tries to get hold of financial data
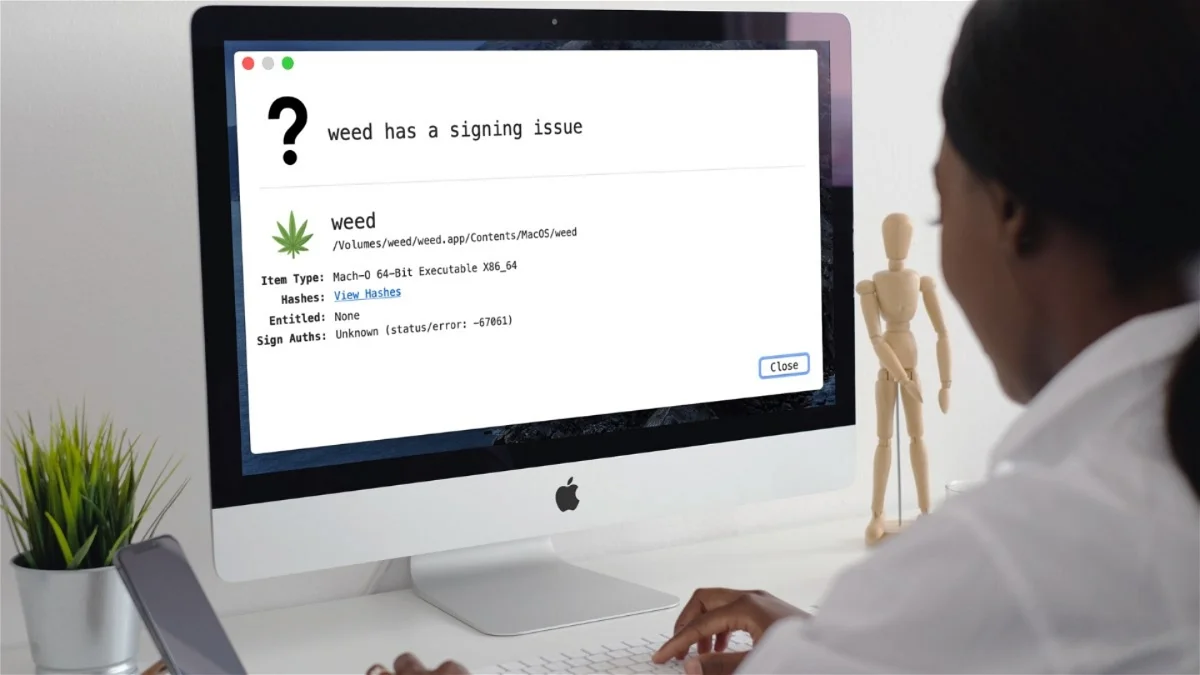
Uptycs discovered MacStealer’s existence through a search of the “dark web.” The creator of this malware is promoting its capabilities and making it available to criminals for $100 per build. Unlike other macOS malware, it is not yet known how the “weed.dmg” file is distributed, but opening this DMG file is enough to infect a Mac.
The researchers explained that the malware collected the data, compressed it into a single zip file, sent the file, and then deleted it from the Mac. So far, Apple has not commented on this:
It’s unclear whether MacStealer is registered with the CVE.report database, which tracks vulnerabilities and risks, and Apple hasn’t commented on the malware. Apple released updates for macOS Big Sur, Monterey, and Ventura on Monday, but these updates don’t appear to include patches for MacStealer, according to the security notes.
Although it poses a significant risk, MacStealer is easily detectable by Gatekeeper and will block it on most Macs running macOS Catalina or later with Intel or Apple’s M-series chips targeted by this virus.
while Distributed by an app called Weed, with a marijuana symbol may not seem like a safe thing to many users. But when it doesn’t, it achieves its purpose by running the app manually and then you have to enter the Mac password to grant access to System Settings for it to work.
No doubt and although there are many warnings to get rid of this malware, its existence reminds us once again the importance of downloading apps from Mac App Store or trusted developer websites.
Source: i Padizate