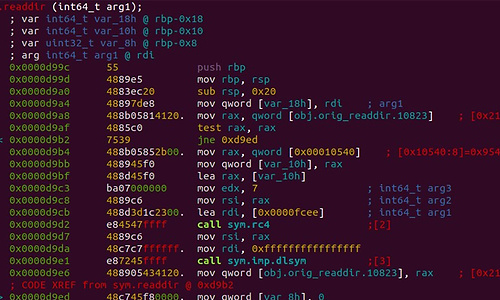
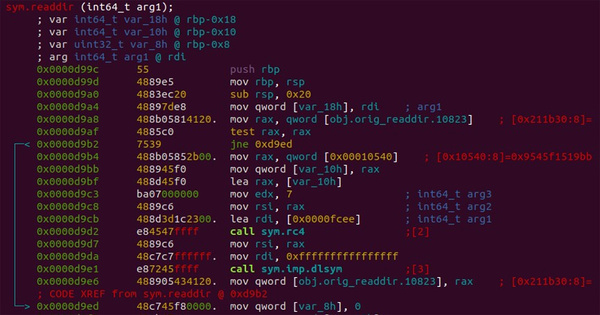
Researchers at Blackberry and Intezer have published information about an elusive Linux malware known as Symbiote. Unauthorized users are given the option to collect credentials or gain remote access to the computer. Once infected, all malware becomes hidden and undetectable.
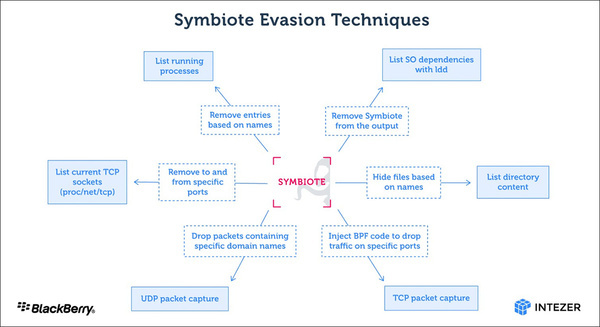
The threat presents itself as a shared object library (SO), rather than a common executable that users must run to infect a host. Once infected, SO is loaded into currently running processes on the target computer. Affected computers gain the ability to collect credentials, exploit remote access, and execute commands with unauthorized elevated privileges. Malware is loaded before other shared objects via the LD_Preload directive and is prevented from being detected. The malware installed first can also use other installed library files.
In addition, Symbiote can hide network activity by creating certain temporary files, hijacking the bytecode of infected packet filters, or filtering UDP traffic using certain packet capture functions. There is a detailed explanation on Blackberry and Intezer’s blog.
The research team first discovered the malware in 2021. Since then, the team has determined that the malware does not share code with other known malware, classifying it as an entirely new malware threat for Linux operating systems. Administrators can use network telemetry to discover abnormal DNS requests. In addition, statically linked antivirus, endpoint security and response (EDR) tools can be used to ensure that user-level rootkits do not infect target machines.
Source: Blackberry
Source: Hardware Info