A new attack called Hertzbleed makes it possible to obtain complete cryptographic keys by observing changes in clock frequency. These fluctuations are caused by dynamic voltage and frequency scaling, where the frequency depends on the power consumption and the data being processed.

The vulnerability was discovered and made public by a research team from the Universities of Austin, Illinois Urbana-Champaign, and the Universities of Texas in Washington. Riccardo Paccagnella says on Twitter that this is a real and practical threat to remote servers that were previously deemed safe. The article “Hertzbleed: Transforming Powerful Side-Channel Attacks into Remote Timing Attacks at x86” will be presented at the USENIX Security Symposium August 10-12 in Boston.
The attack can be carried out remotely via the power side channel without the need for a measuring device. Even cryptographic code implemented in constant time is vulnerable. Constant time indicates that no matter the size of the input, the algorithm must always go through the same number of steps and always takes the same time to execute.
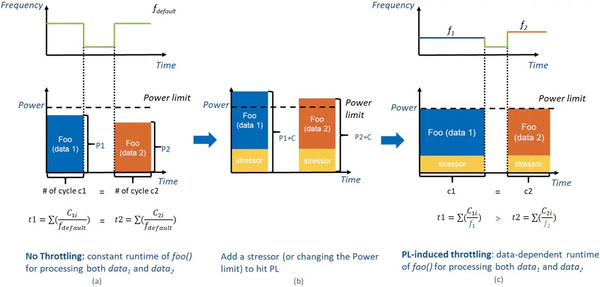
Intel explains how power limits cause interruptions, making runtime or execution time dependent on the data to be processed.
Intel says that all processors are affected and the attack can be carried out with few rights for the attacker without the user needing to do anything. Zen 2 and 3 processors are being hit at AMD for server, desktop, mobile and Chromebook. It is possible that CPUs with other architectures such as Arm that also use frequency scaling will be affected as well, but this has yet to be tested.
According to an Intel spokesperson, performing the attack outside of the lab is impractical and the company has no plans to release patches. The researchers say disabling the frequency boosts can prevent information leakage, but they don’t recommend it because of the performance losses that come with it. Intel even says that this has no effect on the vulnerability.
AMD recommends that the software in which the encryption operations are performed is better protected with algorithms to hide the keys. Intel also recommends making the software more secure. Neither manufacturer offers concrete solutions for this vulnerability.
Source: Bleeping Computer
Source: Hardware Info