Millions of Linksys and Netgear routers and other IoT products are affected by an unresolved DNS vulnerability. Security researchers at Nozomi Networks Labs discovered CVE-2022-05-02, a dns implementation bug in two popular C libraries. uClibc and uClibc-ng are mostly used in routers and IoT products.

The manager says they couldn’t develop a solution themselves. That’s why the 30-day delay vulnerability was finally released in hopes that someone else could apply a fix. In addition to Netgear and Linksys, Axis Communications also uses the uClibc library, like the Linux distribution Embedded Gentoo. uClibc-ng is a fork specially designed for router OS OpenWRT.
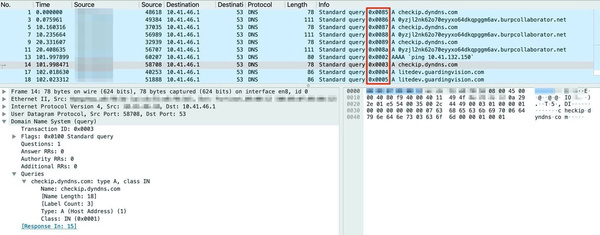
The transaction IDs in the red frame are predictable.
The vulnerability stems from the predictability of transaction ID numbers. These are created when processing dns requests. By detecting process IDs, attackers can perform so-called DNS poisoning. If a user enters a web address, an incorrect IP address is returned.
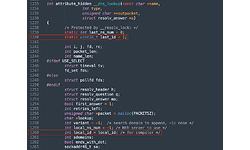
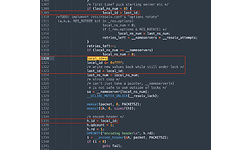
The last_id value can be guessed and populated by the attacker.
As a result, victims can be redirected to malicious websites unnoticed. The attacker can steal or change the information and further attack the device. The main problem is that it is difficult to determine whether a correct or toxic IP address has been returned.
Due to the severity of the vulnerability and the lack of a fix, no details about the affected devices have been disclosed.
Source: Bleeping Computer
Source: Hardware Info












