Yesterday news broke that Chinese police helped file senders via AirDrop. Now it’s clear how this is possible.
Macworld was able to reproduce the entire part of the attack. Macworld employees launched the console on a Mac and sent a file from an iPhone to it.
It turns out that the sharing process is responsible for AirDrop. It contains a special subprocess called AirDrop, but several other subprocesses were also activated during the file transfer. In one of the subprocesses, journalists found the name of the iPhone from which the files were sent.
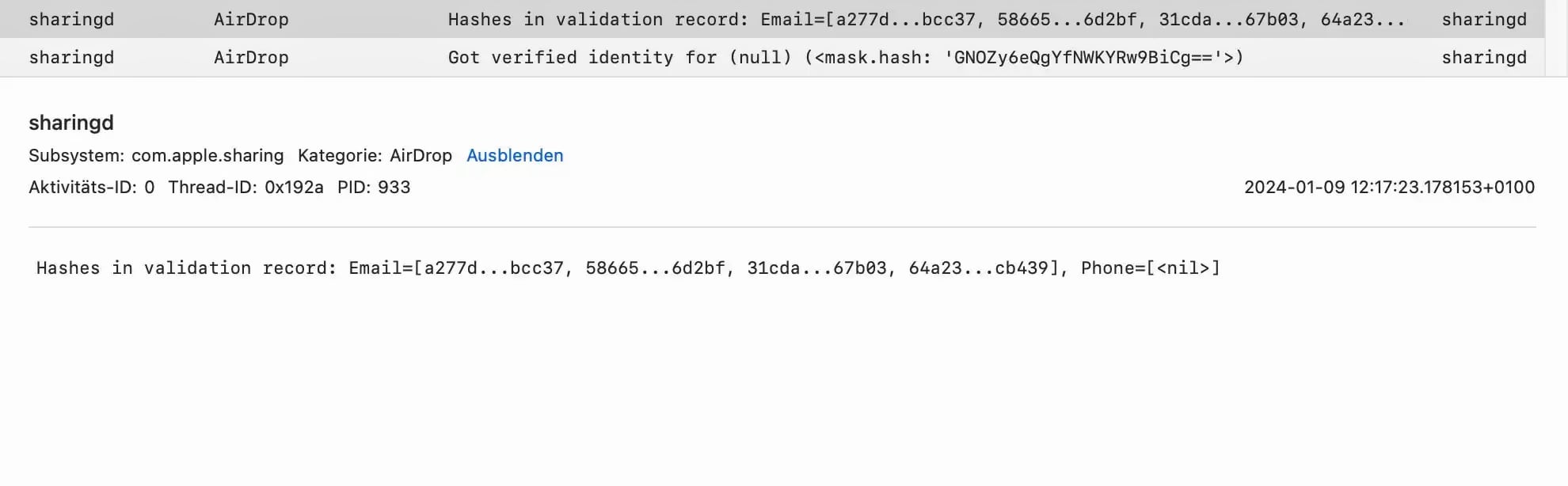
The AirDrop subprocess also saves the phone number and email address of the iPhone used to send files as hash values.
It is likely that Chinese hackers were able to crack the hashes and obtain the encrypted data.
Security experts have been warning Apple for years that it is unsafe to store AirDrop sender numbers and emails in video hashes. The warnings date back to at least 2019.
Alexander Heinrich from the Technical University of Darmstadt reported this issue to Apple in 2021 while iOS 16 was being developed. Apple responded to him but took no action. [Macworld]
Source: Iphones RU
I am a professional journalist and content creator with extensive experience writing for news websites. I currently work as an author at Gadget Onus, where I specialize in covering hot news topics. My written pieces have been published on some of the biggest media outlets around the world, including The Guardian and BBC News.