PlayStation Portable can be called a real people’s portable in our country. In no case does it owe its status to the fact that games on it could be downloaded for free, and most of the consoles sold were hacked in advance.
But how did hackers manage to break through the security of the second Sony laptop? What were the difficulties in this process and where did Greek mythology originate? I will talk about all this in this material.
First steps. All that was required to run pirated apps was caution.

Sales of the PlayStation Portable (PSP) began in Japan in 2004. A console with firmware version 1.0 and an engineering vulnerability appeared in stores, which the developers forgot to close. Thanks to this miscalculation, it was possible to run unregistered code. It was only necessary to understand in what format the executable files in the system work and by what logic the entire operating system as a whole works.
In 2005, a hacker under the nickname Nem was able to do this. How?

The console’s launch lineup included Wipeout Pure, an excellent racing game that supports downloadable additional content (DLC). By downloading the DNS spoofing DLC path, it was possible to launch a full-fledged browser (at that time it was hidden from the user). Through the browser it was possible to get to the file system, the first entry into FS. He was able to dump the firmware and understand how to run external programs on the console.
The first launch was carried out through a simple script, which displayed the inscription “Hello World!” on the screen. However, before the launch of the first games, there was still time from the console itself, because the vulnerability was not saved much differently than the disk image. Therefore, first of all, the PSP was filled with ports of DOOM (by the way, the port of the famous YouTuber MVG) and famous emulators.
Sony is trying to correct its own mistakes… And making new ones
In 2005, Japan PSP went beyond borders. The American and European versions already had firmware 1.50 on board, the vulnerability of which was covered. Sony tried to update the rest of the consoles by sending updates over the air.

However, even in 1.50 there was a switch to the console mode for launching unregistered program code. To do this, while loading the game, you had to sharply pull out the memory card and insert another one. The abilities are quite barbaric and not always developed. But it was at 1.50 that hackers perfected the work with executive files and learned to rip consoles loaded into games from the memory.

In the meantime, Sony released update 2.00, which, in addition to closing this hole, added several important features – a browser, a media player and the ability to save wallpaper on the desktop. And yes, they shot themselves in the foot again. After all, it was after 2.00 that hackers invented the world famous tiff-exploit.
His conclusion is as follows: you had to throw a transition (and intentionally corrupted) tiff image onto the console, connect the console to the network adapter, open the image using the photo viewer (which was added along with the others to put the wallpaper on your desktop) .
And when the console tried to open the picture, its memory buffer was overloaded to such a state that the same engineering mode and all the possibilities of piracy were opened. By the way, it was this method that made it possible to write a program that rolled back the software version to 1.50, where the hack worked more stable and launched games from the PSP itself.

Sony realized this vulnerability in firmware 2.01, but could not debug the buffer protection so that it did not open the way for unregistered termination code to run. 2.01 could also be broken, but in a more exotic way. You need a GTA Liberty City Stories disc with the game brand 1.0. Saving this version of the game allowed the memory buffer to overflow and… yes, activate a hack. And most importantly, the next few software errors could not completely close the hole in the protection. The problem was solved only with the help of Rockstar, which released an updated version of the disc, where the problem with the save was fixed.
But Sony did something too. New games began to require the latest firmware version to run, and this problem could not be overcome for a long time. Until HE showed up.
Dark Alex and the PSP Piracy Revolution

Everything that I described above turned out to be a way to unlock the launch of games without checking licenses and home-written programs, but it was still based on the kernel of the official firmware 1.50 and blocked access to both new functions of the PSP itself and to new games that required higher firmware. An anonymous hacker under the nickname Dark Alex was able to solve this problem by creating custom firmware.
With its help, it was possible to both launch current games, deceiving system version checkers, and use all the current functionality of the console and even more. For example, it was possible to overclock the processor, and this really makes games run more stable and faster.

This is what the PSP looks like when it’s bricked; beyond that, the on-screen console doesn’t turn on.
However, along with this, ill-wishers appeared who, under the new firmware, spread a virus that turned your PSP into a broken brick without the possibility of recovery. In the meantime, all minor vulnerabilities in the first versions of the PSP have been fixed. However, with the release of the second revision of the console in 2007, installing unofficial firmware became a very risky endeavor.
Panic over the Slim console and Pandora battery as a panacea for all problems
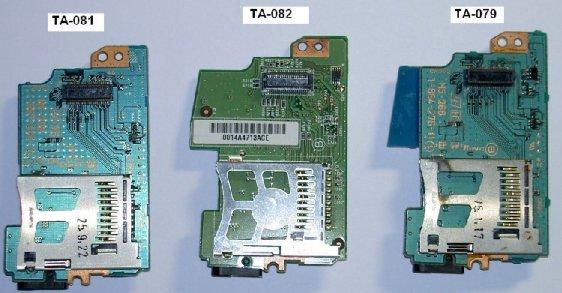
TA-082. Many who were fond of PSP in the 2000s probably have a pang in their chests now. What is this character set? This is the marking of the board in the updated revision of PSP Slim. If microorganisms flash a PSP with this motherboard, you are guaranteed to get a brick. They didn’t immediately learn to determine the version of the board in advance, and many people slowly killed their console with an attempt to hack it.

Pandora’s kit is visible.
The decision did not come immediately. In 2007, the Noobz team introduced the peak of hacking capabilities to the PSP community. This solution was called “Pandora’s Battery” and was a set of a flash drive with software and a specially modified battery from the PSP. Using this kit, it was possible to launch the console, bypassing the official OS bootloader, directly in the bootloader located on the memory card, and thereby remove the block of the official bootloader (the same “bricking”). Also, using Pandora, it was easy to downgrade the firmware version to a vulnerable one (only on the Fat version of PSP).
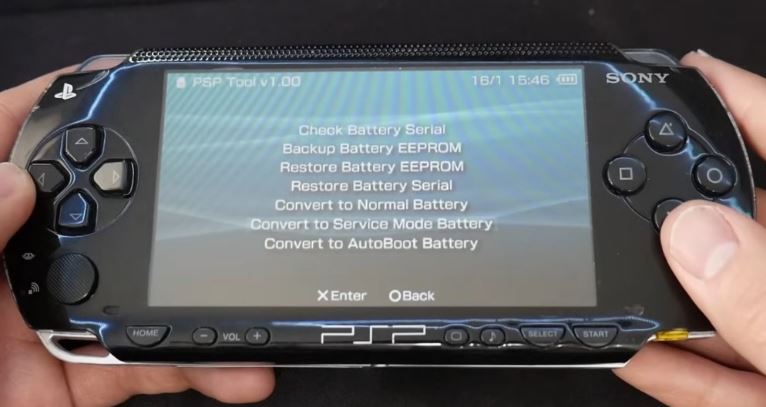
Consequences of Pandora’s launch. Here you can install any firmware
Team Noobz was also able to find a vulnerability in the current version of the software. This time the console was flashed using the game Luminies and the memory buffer was reloaded again. And I modified the Pandora battery itself and the software in such a way that with its help they learned to break the non-flashable TA-082 board. By the way, there is an interesting point connected with it. This motherboard was not installed in all versions of the PSP Slim 2000, starting with revision 3000, and PSP Go was no longer used at all, because Sony believed that their firmware was completely protected at the software level.
Nominally this was the case, the current version of the firmware did not break on its own for a very long time, but with the help of a Pandora battery, the side console could be put into service mode, bypassing the official software, and any modified firmware could be installed from under it.
PSP Go and PSP 3000 as Sony’s last bastion

PSP Go was one of the last to be hacked, as all vulnerabilities were closed and the memory card format was changed
Nominally, no major events occurred in the PSP hacking scene after the invention of the Pandora Battery. Nominally. There was one more important nuance that slightly spoiled the lives of owners of the latest revisions of the console. It so happened that the PSP Go and PSP 3000, although it was possible to flash them, were hacked when the console was rebooted or turned off (like an undeclared jailbreak, yes).
And this problem was finally overcome only in 2016. The hacker Davee released the ultimate and latest custom firmware called Infinity 2.0. It appears on any version of the console, does not crash and gives the maximum number of hacking features. This is where the PSP hacking story officially ends.
Long afterword of Sony’s war with pirates
The corporation lost a fierce war with groups of enthusiasts. It is worth giving Sony their due – they fought fiercely and honorably, constantly patching holes in vulnerabilities and, as a result, rushing to create new ones. The final point in the confrontation between Sony and hackers was the Pandora Battery. Sony itself recognized the device and even used it in its service centers to restore bricked consoles.

In addition, it was PSP piracy that inspired Sony to add the ability to install Linux on the PlayStation 3, in connection with which the former president of the representative division. And he was officially told that homebrew on the console looks the same as they (Sony) wanted to do for themselves.
In this laptop, engineers and programmers have significantly improved the security, and the PS Vita will be impenetrable to complete hacking for many years to come. But in 2016, the console succumbed, and through the built-in browser (yes, like the first PSP hacks), a system vulnerability was discovered. However… This is a completely different story.

And that’s all I have. While working on this intervention, I had to re-read old official forums, including Western ones, and you know, it was damn interesting. I deliberately did not put myself in danger when developing custom firmware on the console, otherwise the article would have turned into a huge set of numbers and names. All the most popular ones, I’m sure you know in the comments, what was on your PSP: maybe 5.50 GEN-3 or Prometheus? Thank you for reading to the end and have a nice day!
Source: Iphones RU
I am a professional journalist and content creator with extensive experience writing for news websites. I currently work as an author at Gadget Onus, where I specialize in covering hot news topics. My written pieces have been published on some of the biggest media outlets around the world, including The Guardian and BBC News.










