Data on a computer is often found even in more animals than the PC or laptop itself. Restoring them can be very difficult, once in the environment, they can have significant harmful effects.
We offer you to install 10 standard macOS options that significantly increase the level of protection of confidential information on your Mac.
1. Set a complex unlock password
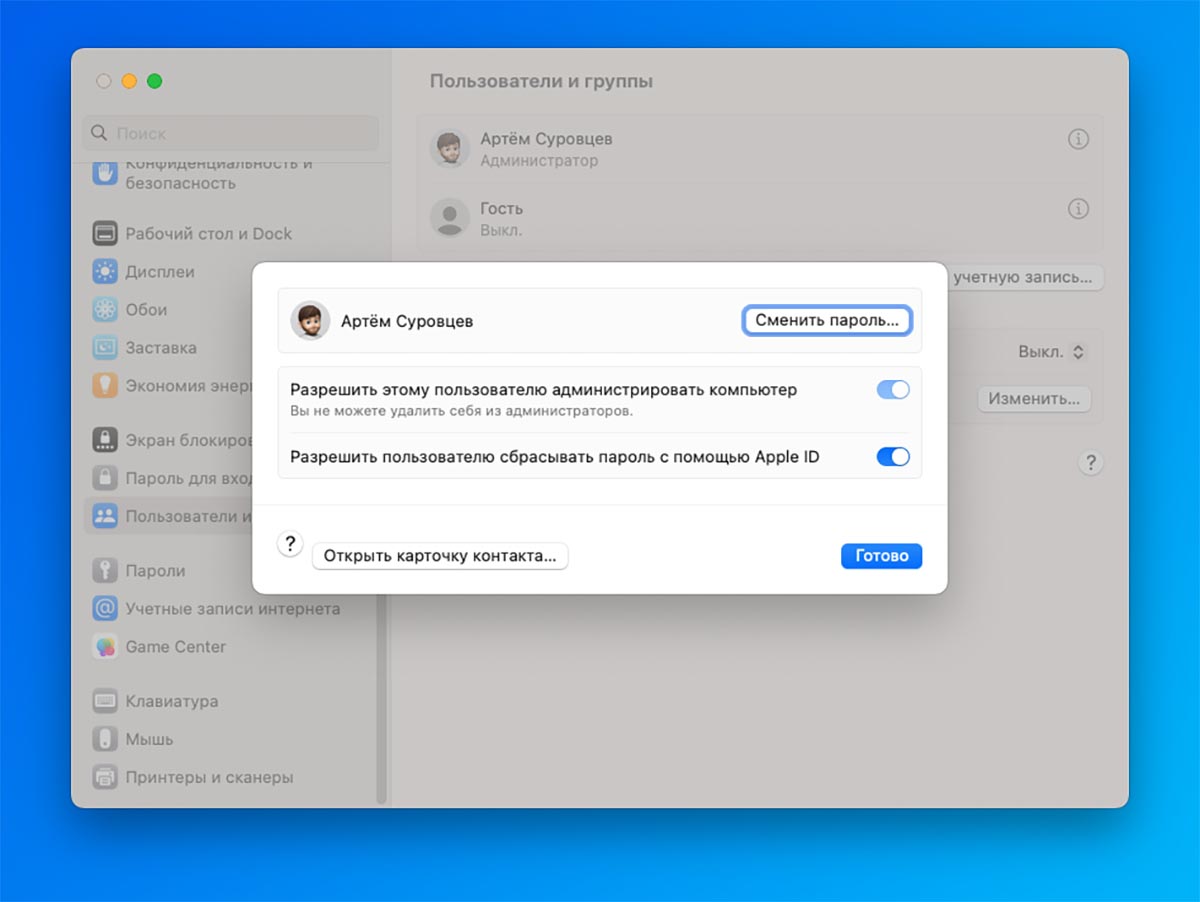
Do not neglect the most modern and effective ways to protect Apple computers. If you set a probable password, the probability of its selection is minimized. He did not have the opportunity to casually observe other patrons in a cafe or colleagues in the office.
How to setup: transportation System Preferences – Users & Groups and change the unlock code for your account.
2. Shorten the suspension interval.
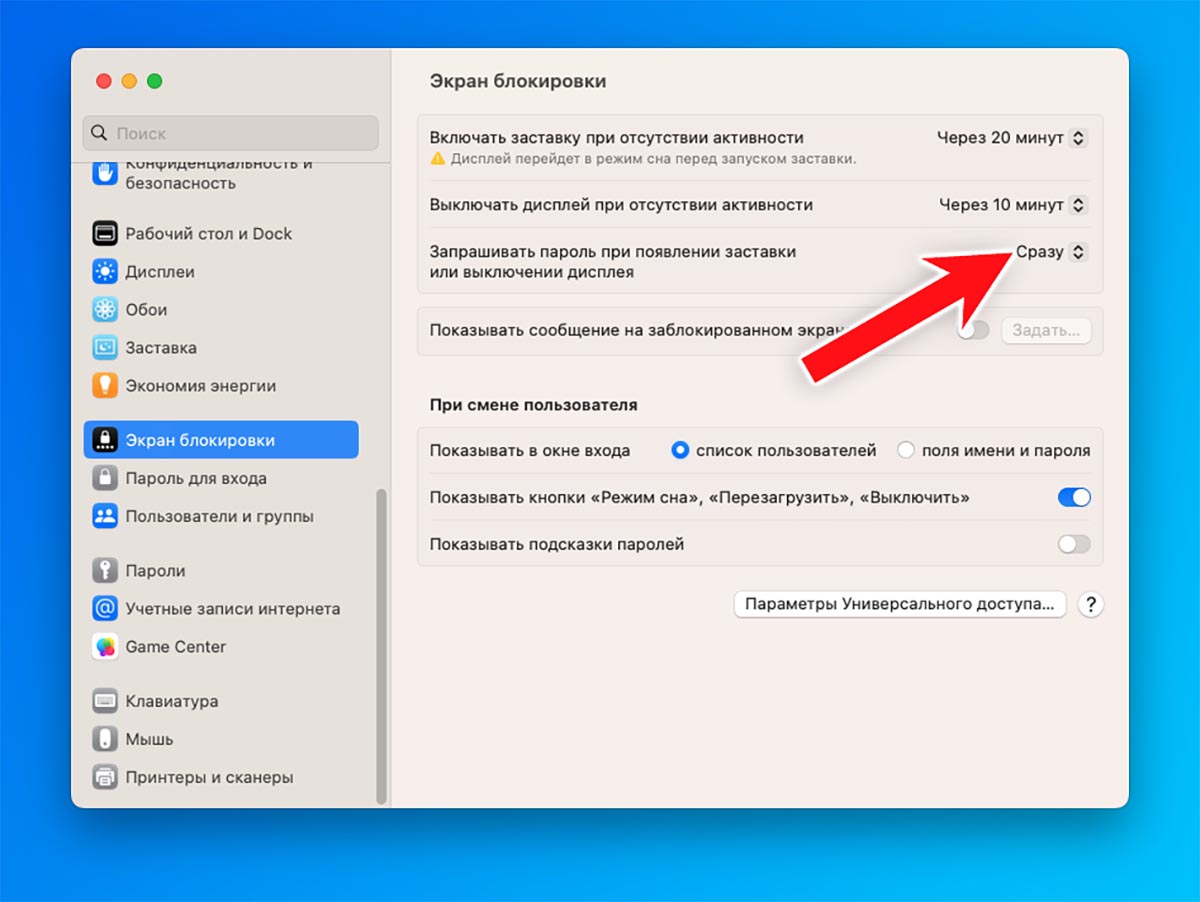
If you often work with a computer in a public place, be sure to reduce the request to the limit value of the interval. So after the screen saver is activated or turned off, the computer screen will be immediately affected by the unlock code.
Use Touch ID a little more often, but if you leave your MacBook for a while, it will lock up faster.
How to setup: ease System Settings – Lock Screen and set an instant lock when the screen turns off or the screen saver is activated.
3. Set up a quick lock system.
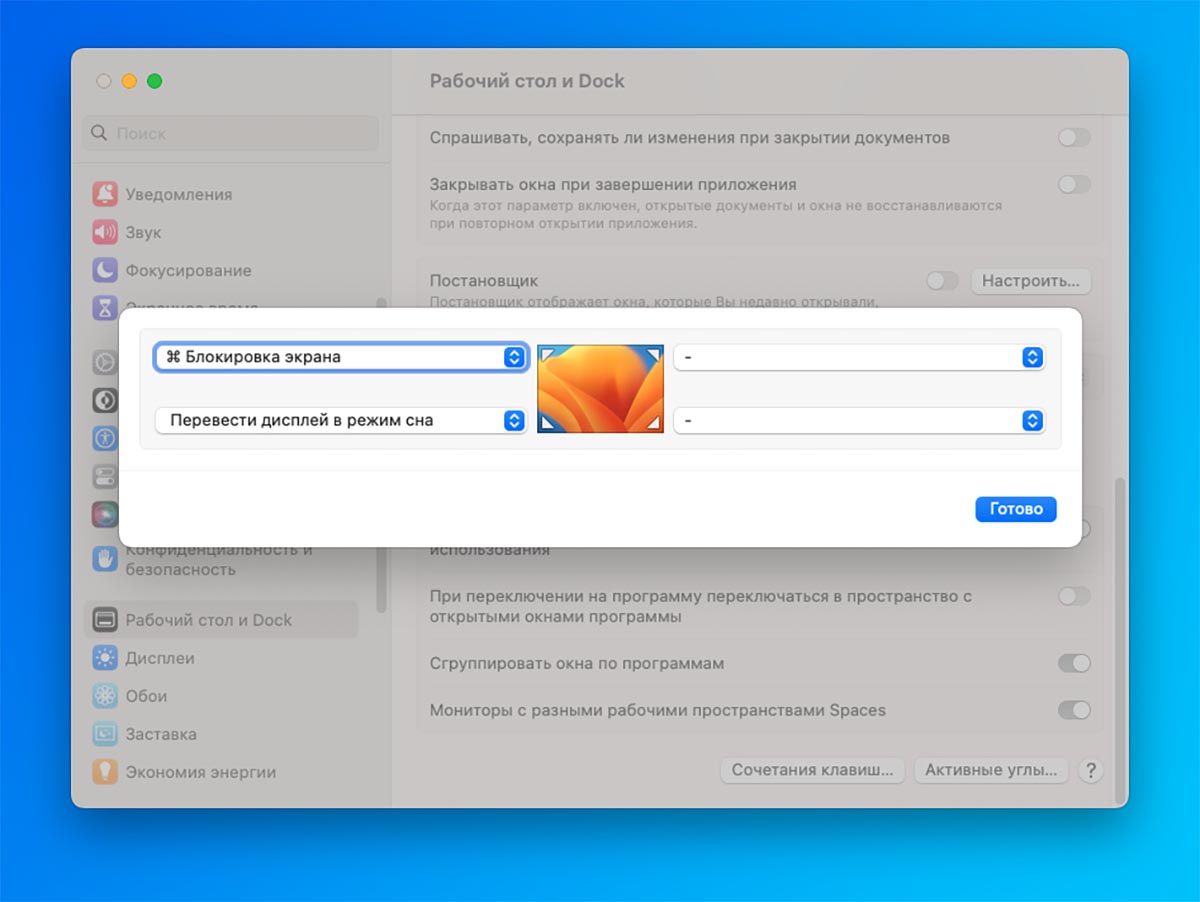
Once set up, be sure to make it a rule to lock your Mac when you step away from it. There are several ways to do this: learn keyboard shortcuts Command + Control + Q or blocking from the menu bar – Lock screen.
There is a more convenient way – to set the active corners. With their help, you can block the rotation of the detector, turn off the display or activate the screensaver.
How to setup: transportation System Preferences – Desktop & Dock and press the button Active corners at the very bottom of the list. You can set different actions for each corner, and to exclude false actions, you should add a modifier.
4. Turn on sign out when your Mac is idle
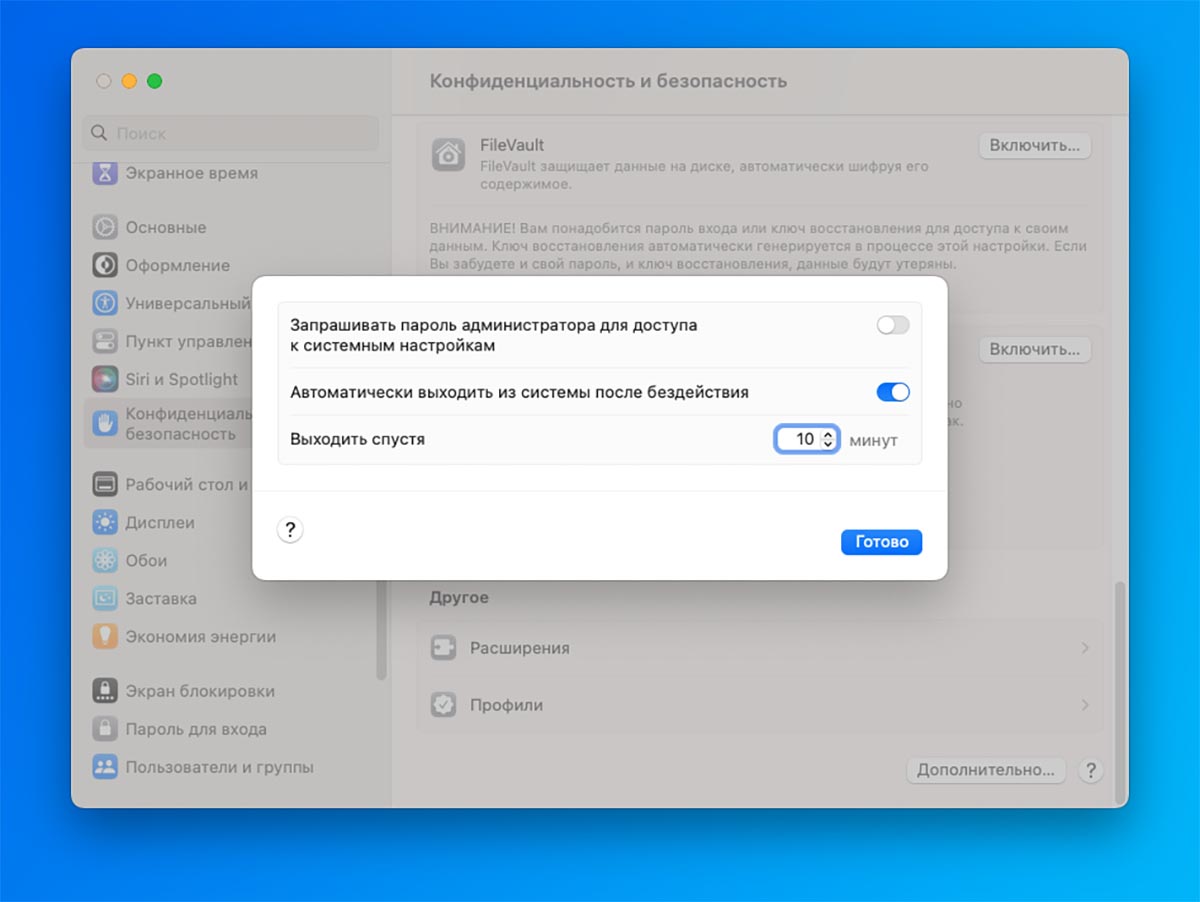
Another option that allows you to lock your computer when idle. When the device is left unattended for a long time, the system will not only lock the screen, but log out of your account. This is especially useful when automatic account selection is disabled on the Mac and you need to enter not only the password, but also the login.
How to setup: to activate health System Preferences – Privacy & Security at the very bottom of the list, find the item Additionally activate toggle switch Automatic distribution from the system after inactivity.
Below you should set the comfort interval.
5. Enable FileVault Encryption
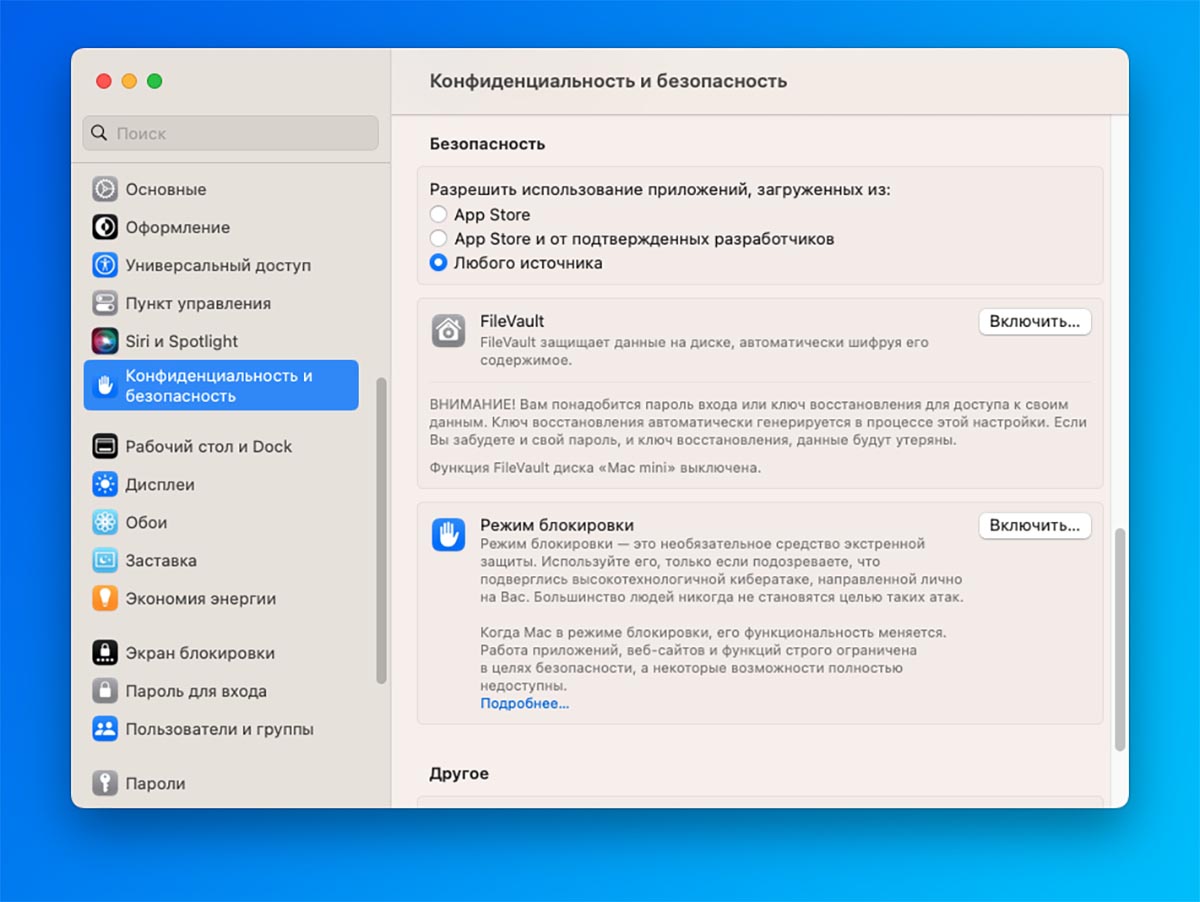
File Vault is a built-in data encryption system that is used in the event of a computer hack. If it is activated, then it will be very difficult to get data from the drive. Even if you dismantle the SSD and connect it to another computer, data with such an account will not work.
How to setup: transportation System Preferences – Privacy & Security – FileVault and drive encryption. On computers, this may seem like a longer system boot time.
6. Turn off unused sharing options.
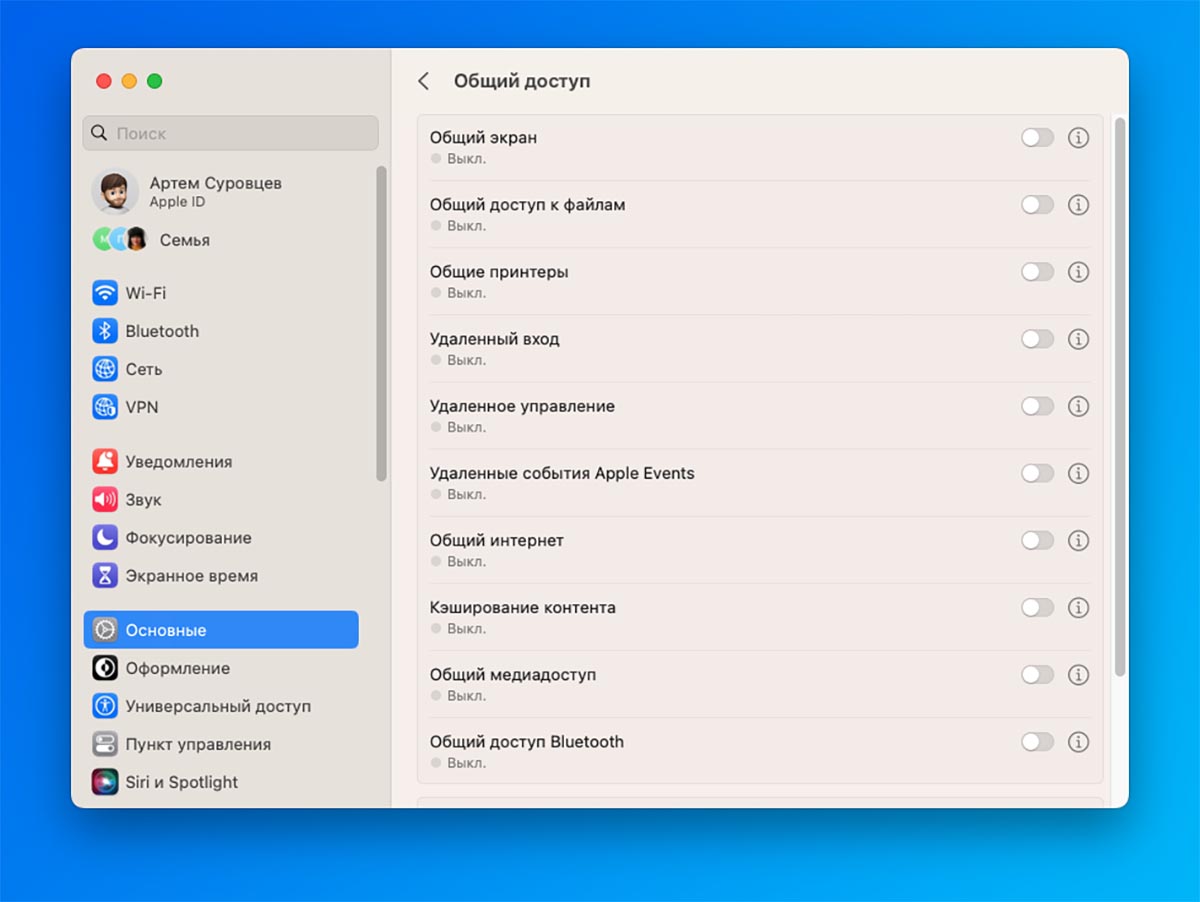
Another weakness in the discovery system is data sharing, the computer screen, and the ability to connect remotely. Chips are needed to operate specific software or provide access to a computer for other users. Many Mac owners can’t imagine that it’s better to choose options in General Preferences.
How to setup: transportation System Preferences – General – Sharing and turn off the chips that are not involved in working with the computer.
7. Activate the firewall
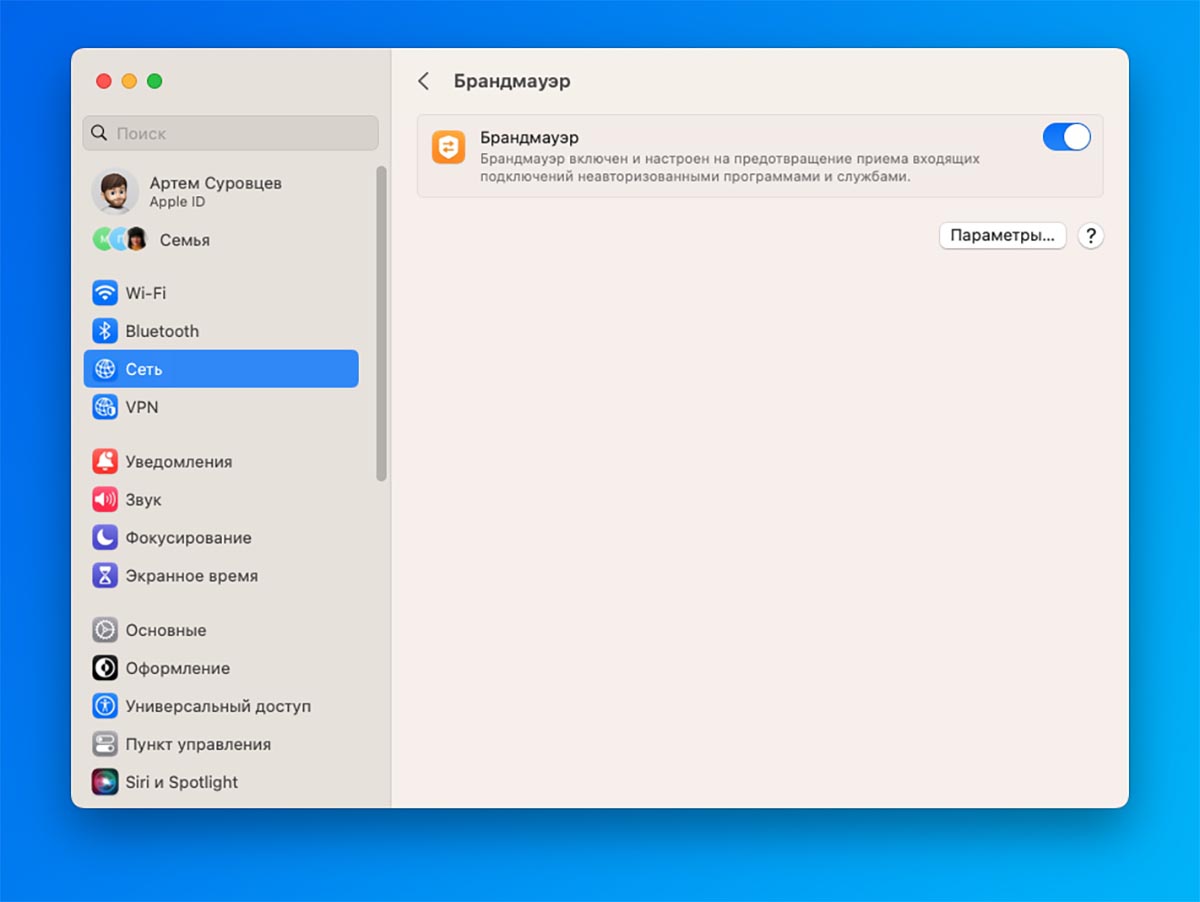
Additional protection against network attacks can be built into macOS Firewall. The system will block suspicious incoming connections and may prohibit the prohibition of the use of prohibited substances for the operation of software and network services.
How to setup: ease System Preferences – Network – Firewall and activate the main toggle switch. If necessary, strengthen the protection in the advanced parameters of the same settings section.
8. Set up multiple macOS accounts
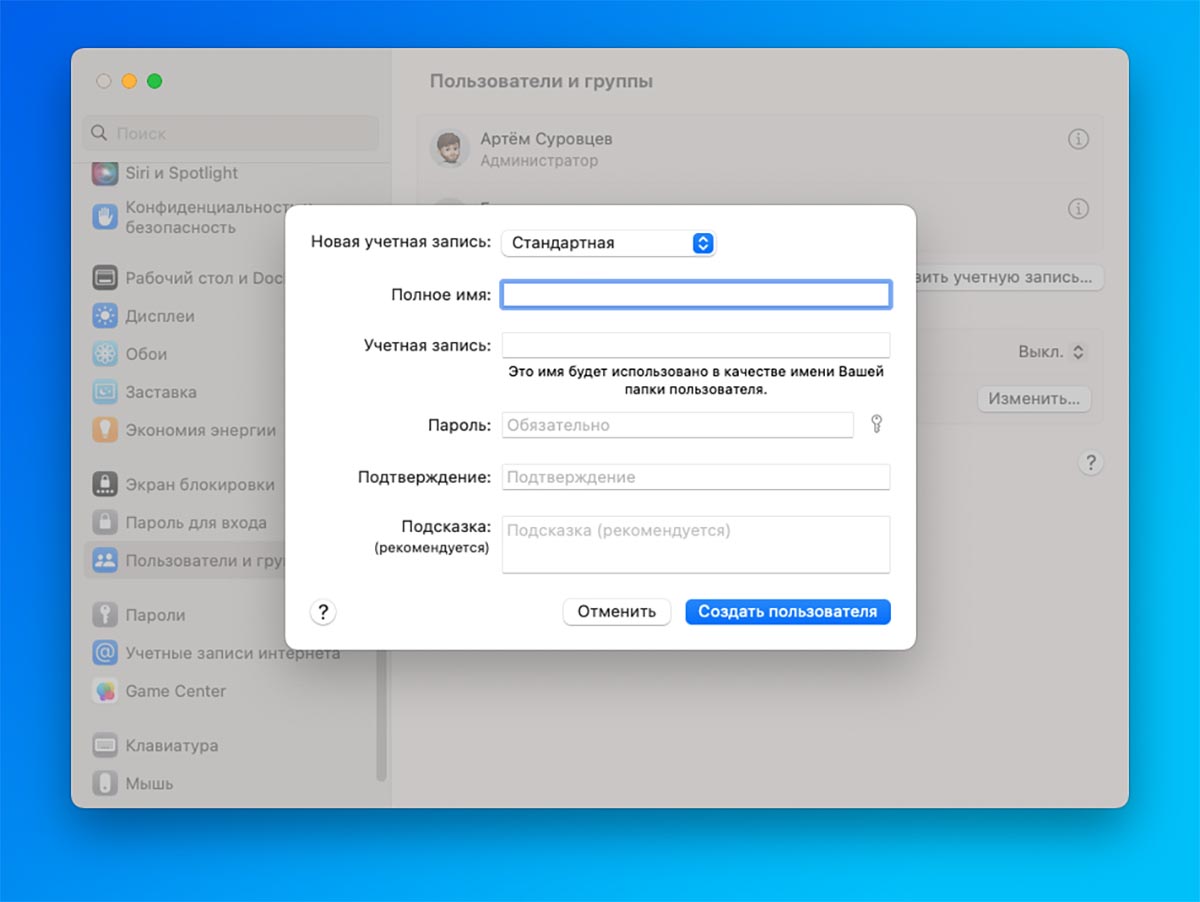
If other family members, children or work colleagues often work at the computer, it would be useful to create several accounts for them. Most frequently used Macs are advised to create separate accounts, and for occasional users, a guest account is recommended.
How to setup: accounts are managed in the section System Preferences – Users & Groups. You can read more about what happened and different types of records here.
9. back up often
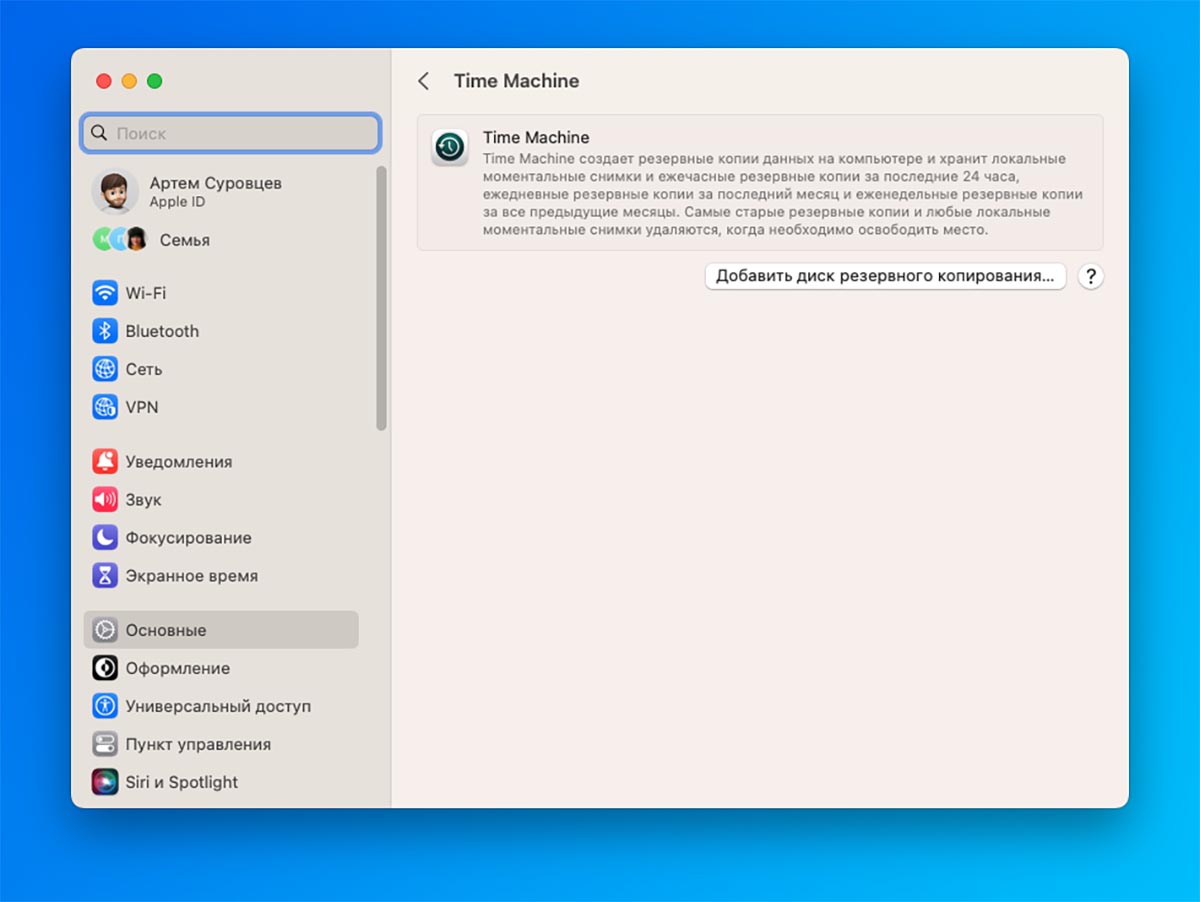
In case of theft or loss of a computer, it is advisable to use all the data. So you can deploy a system with all the necessary applications and files on expensive valuables and quickly include in the workflow.
How to setup: nothing simple standard system Time Machine for Mac has not been invented yet. Go to section System Preferences – General – Time Machineconnect an external or network drive for backups and set up a backup connection.
10. find find mac
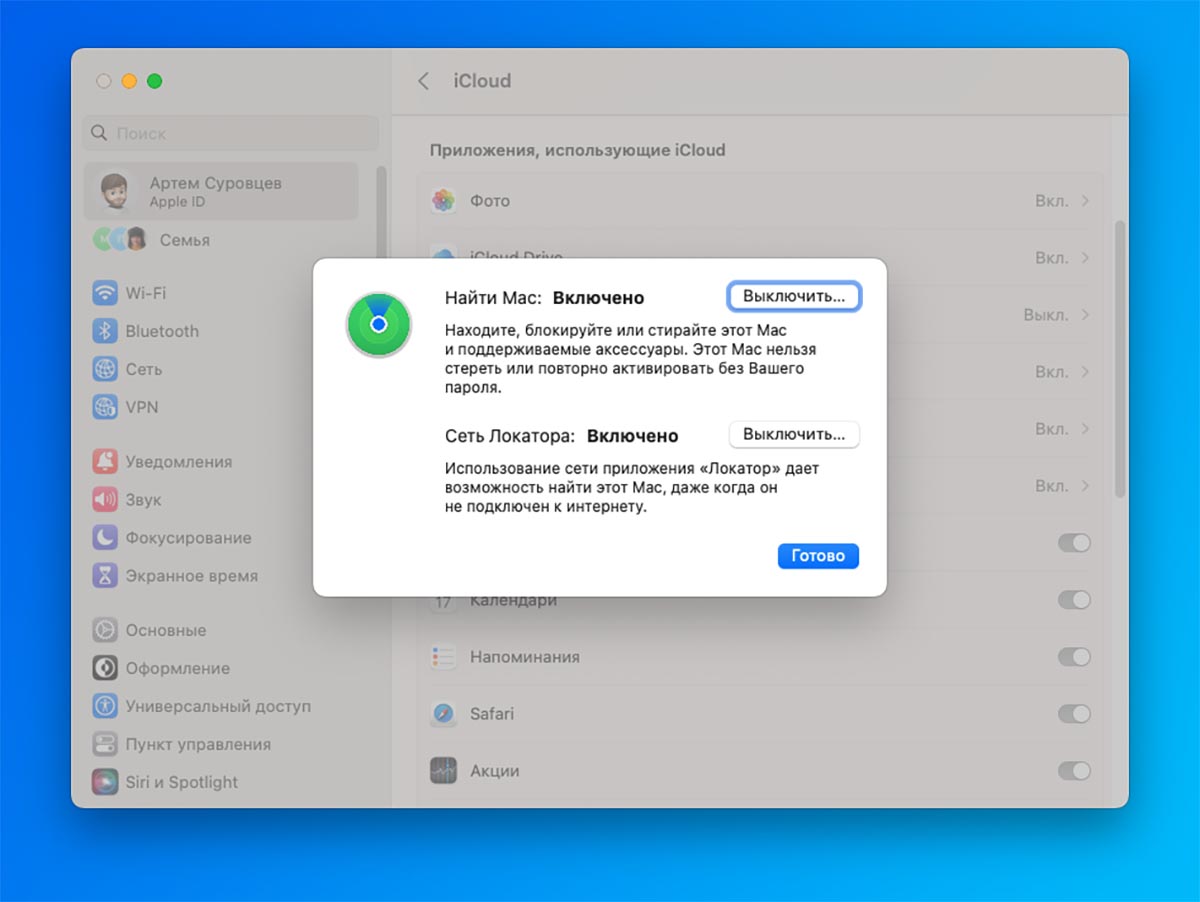
This feature is required for use not only on the iPhone, but also on Mac computers. Connecting to a network stolen or lost computer can be detected through the application Locator to any device with your Apple ID account. Recently, it will be possible to find a gadget, even if it is not connected to the Internet, but there are apple devices of other users nearby.
How to setup: ease System Preferences – Apple ID Account – iCloudpress the button to display all applications for cloud integration and activate the view Find a Mac.
Now data about the upcoming Mac will be as protected as possible from attacks on the network, in case of loss or theft of the computer.
Source: Iphones RU
I am a professional journalist and content creator with extensive experience writing for news websites. I currently work as an author at Gadget Onus, where I specialize in covering hot news topics. My written pieces have been published on some of the biggest media outlets around the world, including The Guardian and BBC News.










